Skip to content
Network Interface Card (NIC)This card is installed on your computer to connect or interface your computer to the network. It provides the physical, electrical, and electronic connections to the network media.Called a Layer 2 Device because the information it uses for communication (MAC address) is located on the Data Link Layer.Is either an expansion card that is inserted into the PC, or it’s built in by the manufacturer. Today almost all NICs are built-in into the motherboards providing 10, 100, & 1000 megabits per second network connection speed.Layer 2 SwitchThese devices connect multiple segments of a network together much like hubs do, but with 3 Key differences.A switch recognizes frames and pays attention to the source and destination MAC address of the incoming frame as well as the port on which it came in.A switch makes each port of its port a unique, singular collision domain.Switches use hardware MAC addresses to make forwarding decisions.A switch connects network hosts (like computers, other switches, and routers) to each other on the same network. Example Scenario 


 RouterA network device used to connect many different networks and network segments together, combining them into an internetwork. A well configured router can make intelligent decisions about the best way to get network data to its destination. Routers use IP addresses to make forwarding decisions, so they are considered Layer 3 devices; also known as the Default Gateway. Layer 3 Capable SwitchHubA device that connects all of the segments of the network together in a star topology ethernet network; it’s a Layer 1 Device.A Multi-port Repeater; meaning that if one station sends a broadcast, all the others will receive it. But based on who the broadcast is intended for, only the intended broadcast will actually listen and process it.Seen in small networks, but almost never seen in modern corporate networks due to the amount of network collisions & congestion created by it.Nothing more than a glorified repeater that is incapable of recognizing frames and data structures.
RouterA network device used to connect many different networks and network segments together, combining them into an internetwork. A well configured router can make intelligent decisions about the best way to get network data to its destination. Routers use IP addresses to make forwarding decisions, so they are considered Layer 3 devices; also known as the Default Gateway. Layer 3 Capable SwitchHubA device that connects all of the segments of the network together in a star topology ethernet network; it’s a Layer 1 Device.A Multi-port Repeater; meaning that if one station sends a broadcast, all the others will receive it. But based on who the broadcast is intended for, only the intended broadcast will actually listen and process it.Seen in small networks, but almost never seen in modern corporate networks due to the amount of network collisions & congestion created by it.Nothing more than a glorified repeater that is incapable of recognizing frames and data structures. Image of a Hub
Image of a Hub Access PointAPs are just a hub that accepts wireless clients via an analog wireless signal; APs operate at Layer 2.APs connects computers with wireless adapters to a network in infrastructure mode.The ease of communicating on a network using a wireless AP instead of having to use an Ethernet cable has changed our world forever.APs can only create one collision domain and can run half-duplex , which is why you describe an AP as a Hub.Wireless will never have the same type of throughput, security, and consistency that a wired Ethernet network would.BridgeA network device that connects two similar network segments together. Its primary function is to keep traffic separated on either side of the bridge, breaking up collision domains by using software.Traffic is only allowed to pass through the bridge and reach the connecting network only if there’s data that’s meant for the other side. Bridges are used to connect two segments together or to divide a busy network into two segments.As bridges use MAC addresses to make forwarding decisions, they are Layer 2 devices that make those decisions in software.Bridges are software based, while switches are hardware-based.
Access PointAPs are just a hub that accepts wireless clients via an analog wireless signal; APs operate at Layer 2.APs connects computers with wireless adapters to a network in infrastructure mode.The ease of communicating on a network using a wireless AP instead of having to use an Ethernet cable has changed our world forever.APs can only create one collision domain and can run half-duplex , which is why you describe an AP as a Hub.Wireless will never have the same type of throughput, security, and consistency that a wired Ethernet network would.BridgeA network device that connects two similar network segments together. Its primary function is to keep traffic separated on either side of the bridge, breaking up collision domains by using software.Traffic is only allowed to pass through the bridge and reach the connecting network only if there’s data that’s meant for the other side. Bridges are used to connect two segments together or to divide a busy network into two segments.As bridges use MAC addresses to make forwarding decisions, they are Layer 2 devices that make those decisions in software.Bridges are software based, while switches are hardware-based. Wireless LAN ControllerCentralized Wi-Fi configuration controller that let you configure the complete network on a single device and push the configurations out to the Wi-Fi access points.WLCs greatly reduce the amount of administrative overhead required to manage large enterprise wireless networks.In larger wireless networks it becomes an administrative burden to manage dozens, hundreds or even thousands of wireless APsLoad BalancerCan send incoming packets to multiple machines hidden behind one IP address; Virtual IP address is published to a domain to receive incoming traffic.The load balancer then has a pool of real servers that it distributes the connections to.Load Distribution can be based on round-robin, least number of connections, response time, weighted percentage, or other metrics to evenly distribute the workload to the servers.Proxy Servertype of server that handles its client-machine requests by forwarding them on to other servers while allowing granular control over the traffic between the local LAN and the Internet.When it receives a request , the proxy will then connect to the specific server that can fulfill the request for the client that wants it; Proxy Server operates at the Application Layer.Proxy Servers can also limit the availability for the types of sites that users on a LAN has access to; This can stop people from visiting non-work related sites while on company internet service.Two Type of Proxy ServersWeb Proxy ServerUsed to created web caches which are used when you google a site you’ve visited before. The web proxy “remembers” you, and the site not only loads faster, it sometimes even recalls your personal information by automatically filling in your username.Caching Proxy ServerCaching Proxy Server speeds up the network’s service requests by recovering information from a client’s earlier request. Caching proxies keep local copies of the resources often, which really help minimize the upstream use of bandwidth; These caching serves can greatly enhance your network performance.Cable modemAllows for voice, video, and data (Broad Bandwidth)(usually Internet) to connect from a home or small business to a cable provider’s network; How the ISP provides the initial internet source.Cable modem is installed at the customer’s site and connects to the coaxial cable network. The DOCSIS standard allows both voice and data to share the cable with the standard video TV offerings provided by the local cable company.DSL modemDistributer Subscriber Modem commonly deployed by traditional phone companies that have twisted pair cablingRepeaterA device that receives signals, regenerates, and resends them; It doesn’t make any forwarding decisions, only repeats the signal to keep it going.Commonly used to Boost Copper or fiber connections, extended Wifi network reach, and convert one media to another.Works on Layer 1 of the OSI model.Voice GatewayA network device that helps to convert voice and fax calls between IP network and public switched telephone network (PSTN).Media ConverterUsed when you need to convert from one type of cabling to another type; Example would be converting from Fiber → Ethernet.Intrusion prevention system (IPS)/ Intrusion Detection System (IDS)Intrusion Detection Systems (IDS)Considered to be a monitor mode and just records problems and tells your about them.Monitors inbound and outbound network connections in order to identify suspicious activityIDS cannot detect traffic within encrypted traffic.Intrusion Prevention System (IPS)Work in real time to stop threats as they occur; works inline to actively prevent and block intrusions that are detected based on the rules you set up. IPS’s can send an alarm, create correlation rules and remediation, drop malicious packets, provide malware protection, and reset the connection3 Main Types of Intrusion Detection and DefenseActive DetectionPassive DetectionProactive DetectionFirewallA Firewall protects your LAN resources from invaders that search the Internet for unprotected networks while simultaneously preventing all or some of your LAN’s computers from accessing certain services on the Internet.Basically, Firewalls are your network’s security guards and since today’s networks are almost always connected to the Internet — this makes security crucial. Firewalls are the first technical line of defense for an Internet-connected network.Without a Firewall in place, any network that’s connected to the Internet is essentially wide open to anyone who is a little tech savvy and seeks to exploit LAN resources or access your network’s sensitive information. Stateful FirewallA stateful firewall is a kind of that keeps track and monitors the state of active network connections while analyzing incoming traffic and looking for potential traffic and data risks. This firewall is situated at Layers 3 and 4 of the model. Packet Filtering FirewallA Packet Filtering Firewall is the most basic type of firewall that controls data flow to and from a network. It is a network security solution that allows network packets to move across between networks and controls their flow using a set of user-defined rules, IP addresses, ports, and protocols. Operates at only the Network Layer (3) of the OSI model.Packets are routed through the packet filtering firewall only if they match predefined filtering rules; otherwise, they are declined.
Wireless LAN ControllerCentralized Wi-Fi configuration controller that let you configure the complete network on a single device and push the configurations out to the Wi-Fi access points.WLCs greatly reduce the amount of administrative overhead required to manage large enterprise wireless networks.In larger wireless networks it becomes an administrative burden to manage dozens, hundreds or even thousands of wireless APsLoad BalancerCan send incoming packets to multiple machines hidden behind one IP address; Virtual IP address is published to a domain to receive incoming traffic.The load balancer then has a pool of real servers that it distributes the connections to.Load Distribution can be based on round-robin, least number of connections, response time, weighted percentage, or other metrics to evenly distribute the workload to the servers.Proxy Servertype of server that handles its client-machine requests by forwarding them on to other servers while allowing granular control over the traffic between the local LAN and the Internet.When it receives a request , the proxy will then connect to the specific server that can fulfill the request for the client that wants it; Proxy Server operates at the Application Layer.Proxy Servers can also limit the availability for the types of sites that users on a LAN has access to; This can stop people from visiting non-work related sites while on company internet service.Two Type of Proxy ServersWeb Proxy ServerUsed to created web caches which are used when you google a site you’ve visited before. The web proxy “remembers” you, and the site not only loads faster, it sometimes even recalls your personal information by automatically filling in your username.Caching Proxy ServerCaching Proxy Server speeds up the network’s service requests by recovering information from a client’s earlier request. Caching proxies keep local copies of the resources often, which really help minimize the upstream use of bandwidth; These caching serves can greatly enhance your network performance.Cable modemAllows for voice, video, and data (Broad Bandwidth)(usually Internet) to connect from a home or small business to a cable provider’s network; How the ISP provides the initial internet source.Cable modem is installed at the customer’s site and connects to the coaxial cable network. The DOCSIS standard allows both voice and data to share the cable with the standard video TV offerings provided by the local cable company.DSL modemDistributer Subscriber Modem commonly deployed by traditional phone companies that have twisted pair cablingRepeaterA device that receives signals, regenerates, and resends them; It doesn’t make any forwarding decisions, only repeats the signal to keep it going.Commonly used to Boost Copper or fiber connections, extended Wifi network reach, and convert one media to another.Works on Layer 1 of the OSI model.Voice GatewayA network device that helps to convert voice and fax calls between IP network and public switched telephone network (PSTN).Media ConverterUsed when you need to convert from one type of cabling to another type; Example would be converting from Fiber → Ethernet.Intrusion prevention system (IPS)/ Intrusion Detection System (IDS)Intrusion Detection Systems (IDS)Considered to be a monitor mode and just records problems and tells your about them.Monitors inbound and outbound network connections in order to identify suspicious activityIDS cannot detect traffic within encrypted traffic.Intrusion Prevention System (IPS)Work in real time to stop threats as they occur; works inline to actively prevent and block intrusions that are detected based on the rules you set up. IPS’s can send an alarm, create correlation rules and remediation, drop malicious packets, provide malware protection, and reset the connection3 Main Types of Intrusion Detection and DefenseActive DetectionPassive DetectionProactive DetectionFirewallA Firewall protects your LAN resources from invaders that search the Internet for unprotected networks while simultaneously preventing all or some of your LAN’s computers from accessing certain services on the Internet.Basically, Firewalls are your network’s security guards and since today’s networks are almost always connected to the Internet — this makes security crucial. Firewalls are the first technical line of defense for an Internet-connected network.Without a Firewall in place, any network that’s connected to the Internet is essentially wide open to anyone who is a little tech savvy and seeks to exploit LAN resources or access your network’s sensitive information. Stateful FirewallA stateful firewall is a kind of that keeps track and monitors the state of active network connections while analyzing incoming traffic and looking for potential traffic and data risks. This firewall is situated at Layers 3 and 4 of the model. Packet Filtering FirewallA Packet Filtering Firewall is the most basic type of firewall that controls data flow to and from a network. It is a network security solution that allows network packets to move across between networks and controls their flow using a set of user-defined rules, IP addresses, ports, and protocols. Operates at only the Network Layer (3) of the OSI model.Packets are routed through the packet filtering firewall only if they match predefined filtering rules; otherwise, they are declined. Firewalls are Separated into 3 Different ZonesUntrusted ZoneScreen Subnet/DMZTrusted ZoneEntire process is similar to a physical man-trap.Firewalls have two network connectionsPublic SideThe network connection to the Internet.Private SideThe network connection to the internal network.Image of Firewalls with a Screen Subnet/DMZScreen Subnet or DMZ refers to the use of one of more logical screening routers as a first defense on your network.
Firewalls are Separated into 3 Different ZonesUntrusted ZoneScreen Subnet/DMZTrusted ZoneEntire process is similar to a physical man-trap.Firewalls have two network connectionsPublic SideThe network connection to the Internet.Private SideThe network connection to the internal network.Image of Firewalls with a Screen Subnet/DMZScreen Subnet or DMZ refers to the use of one of more logical screening routers as a first defense on your network.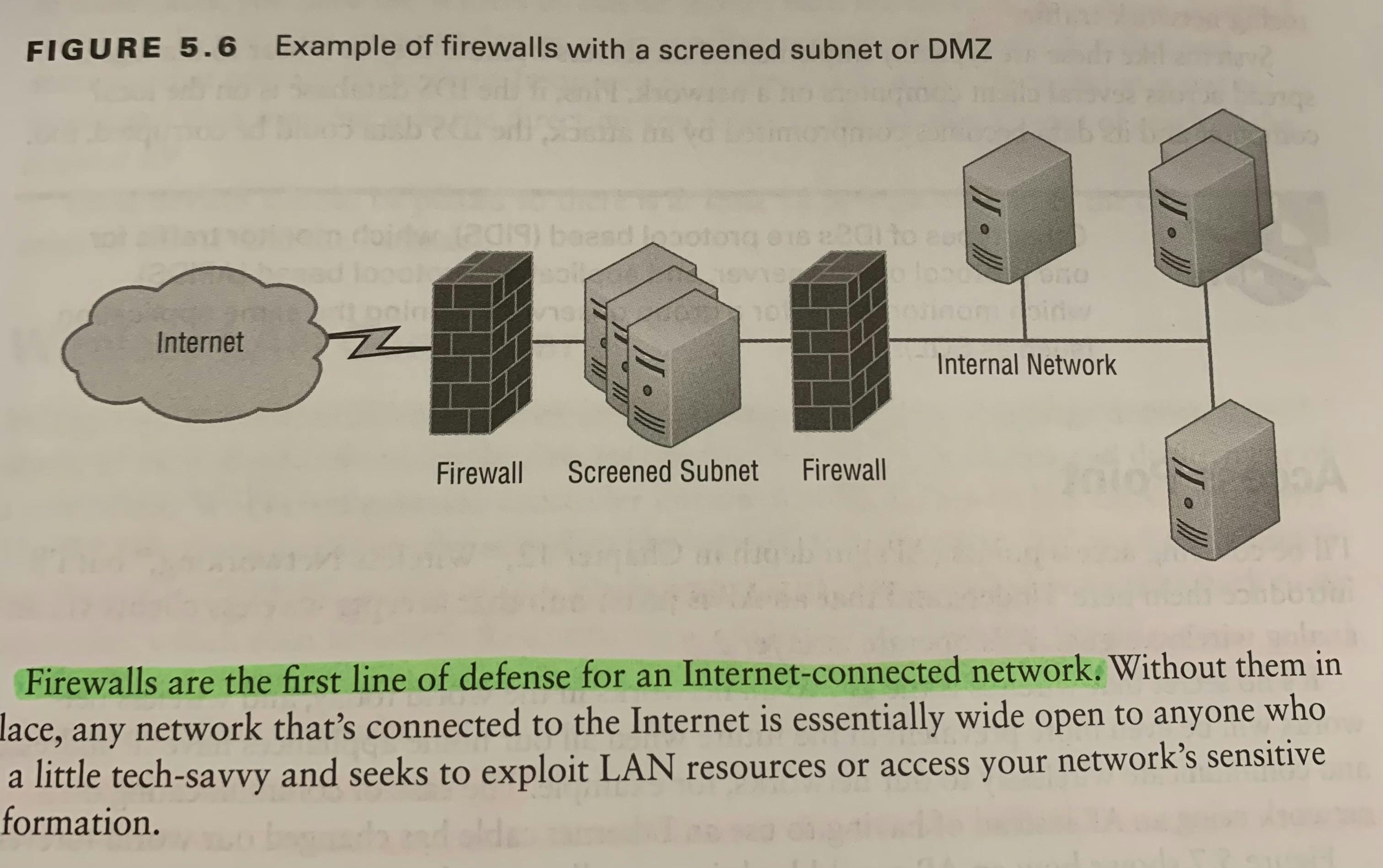 VPN Concentrator/HeadendDevice that establishes multiple VPN connections from remote locations; Dedicating one device to just this one action is better than having a router.
VPN Concentrator/HeadendDevice that establishes multiple VPN connections from remote locations; Dedicating one device to just this one action is better than having a router.
Voice over Internet Protocol (VOIP)Phones have migrated from older analog style to digital ethernet; They tend to be sensitive to delay and jitter, so using some form of QoS is required to keep things running smoothly.PrinterPrinters can be shared on the network with NIC cards or by using a print server to connect all hosts to the desired printer.Physical Access Control DevicesWhenever a user scans their badge at a door, a digital lookup is performed by the server in AD and a response is sent back to the access control device to either unlock the door or prevent a person from entering.CamerasCameras have moved from the analog world to digital and are now very common in today’s networks. They operate off TCP/IP and send video feeds back to a central server for processing and recording.CCTV (Closed Circuit Television)Heating, ventilation, and air conditioning (HVAC) sensors Modern office buildings and industrial sites have intelligent HVAC systems that use sensors to monitor and control air conditioning and heating systems using networking.This allows them to either manually or automatically adjust the environmental controls and has the added advantage of cost saving by changing the temperature values after hours when no one is in the facility.IoT (Internet of Things)Any stand-alone internet-connected device that can be monitored and/or controlled from a remote location is considered an IoT device.Thanks to the advent of inexpensive computer chips and high bandwidth telecommunication, we now have billions of devices connected to the internet. This means everyday devices like toothbrushes, vacuums, cars, and machines can use sensors to collect data and respond intelligently to users. These systems depend on several technologies to facilitate their operations:Z-Wave is a wireless protocol used for home automation. It uses a mesh network using low-energy radio waves to communicate from appliance to appliance. Residential appliances and other devices, such as lighting control, security systems, thermostats, windows, locks, swimming pools, and garage door openers can use this system.ANT+ is another wireless protocol for monitoring sensor data such as a person's heart rate or a bicycle's tire pressure as well as for controlling systems like indoor lighting and television sets. ANT+ is designed and maintained by the ANT+ Alliance, which is owned by Garmin.RFID While RFID is mostly known for asset tracking, it can also be used in the IoT. Objects are given an RFID tag so they are uniquely identifiable. Also, an RFID tag allows the object to wirelessly communicate certain types of information.802.11 Finally, 802.11 can also be used for IoT communication. 802.11 is Wi-Fi tech that can be used to communicate to IoT devices.Industrial control Systems/Supervisory control and data acquisition (SCADA)A technology that uses sensors for monitoring and control of everything from power grids to machines on the factory floor. By monitoring machinery, companies can proactively detect problems and flag the device maintenance, potentially saving money on repairs and downtime.

 2.1 Compare and Contrast various devices, their features, and their appropriate placement on the network.
2.1 Compare and Contrast various devices, their features, and their appropriate placement on the network.
Last edited 1021 days ago by Makiel [Muh-Keel].
What are all of the Networking Devices?









Networked Devices
Want to print your doc?
This is not the way.
This is not the way.

Try clicking the ··· in the right corner or using a keyboard shortcut (
CtrlP
) instead.