Skip to content
Roads are the network topologies and overall layout.This can be made of Ethernet, DSL, coax cableTrucks is the Internet Protocol being used.These topologies were designed for Internet Protocol to run all over them. Outside Boxes are the protocols being used: TCP or UDPBoxes hold the data either using TCP or UDP; Method in which the boxes are being used.Inside the Boxes are more information.Application InformationRooms are the port numbers.Port 443 HTTPS, Port 80 HTTP, Port 22 SSH, etc.
TCP UDPIPv4 SocketsCommon to see port numbers and IP addresses combined into a single series of numbers referred to as a socket.ExampleServer IP address, protocol, server application port numberClient IP address, protocol, client port number Port NumbersTCP and UDP ports can be any number between 0 and 65,535; TCP + UDP use port numbers to communicate with the upper layers because they’re what keeps track of different simultaneous conversations originated or accepted by the local host.Port numbers are for communication, not securityNon-ephemeral PortsEphemeral means temporary or short-lived; so Non-Ephemeral means the opposite: Permanent or constantUsually associate with a service or server; example would Port 22/SSH or Port 3389/RDP; These numbers need to be consistent through out the industry so we can properly communicate using a set standard port number. Also known as Well-Known Port Numbers.
Port NumbersTCP and UDP ports can be any number between 0 and 65,535; TCP + UDP use port numbers to communicate with the upper layers because they’re what keeps track of different simultaneous conversations originated or accepted by the local host.Port numbers are for communication, not securityNon-ephemeral PortsEphemeral means temporary or short-lived; so Non-Ephemeral means the opposite: Permanent or constantUsually associate with a service or server; example would Port 22/SSH or Port 3389/RDP; These numbers need to be consistent through out the industry so we can properly communicate using a set standard port number. Also known as Well-Known Port Numbers. Ephemeral PortsEphemeral ports are used temporarily on a case-by-case basis on an individual client device to be able to communicate with other hosts, and by TCP as source/destination identifiers in the TCP segment..
Ephemeral PortsEphemeral ports are used temporarily on a case-by-case basis on an individual client device to be able to communicate with other hosts, and by TCP as source/destination identifiers in the TCP segment.. MultiplexingMultiplexing is the act of communicating to a device using multiple applications and multiple data types simultaneously.Port numbers are used to help the server differentiate between the different data types when Multiplexing is occurring.Image of Multiplexing
MultiplexingMultiplexing is the act of communicating to a device using multiple applications and multiple data types simultaneously.Port numbers are used to help the server differentiate between the different data types when Multiplexing is occurring.Image of Multiplexing Image of Multiplexing with Port# DetailsPort numbers are used to help the server differentiate between the different data types when Multiplexing is occurring.In the example below referring to the HTTP data packet, you can see that the TCP Source Port is 3000; A random Ephemeral port number being used just for communication. In order to communicate to the upper layers of the OSI model, you need a source port number. In this example, that random number happens to be 3000. In order to properly communicate the correct data type though, you need to know that data type’s well-known (Non-Ephemeral) port number. In the example below, this well-known port number is 80 because HTTP data communicates with port 80.
Image of Multiplexing with Port# DetailsPort numbers are used to help the server differentiate between the different data types when Multiplexing is occurring.In the example below referring to the HTTP data packet, you can see that the TCP Source Port is 3000; A random Ephemeral port number being used just for communication. In order to communicate to the upper layers of the OSI model, you need a source port number. In this example, that random number happens to be 3000. In order to properly communicate the correct data type though, you need to know that data type’s well-known (Non-Ephemeral) port number. In the example below, this well-known port number is 80 because HTTP data communicates with port 80.
Internet Control Message ProtocolWorks at the network layer and is used by IP for many different services. ICMP is a management protocol and messaging service provider for IP. Its messages are carried as IP packets. ICMP packets have the following characteristics.They can provide hosts with information about network problems.They are encapsulated withing IP datagrams.Used for error reporting with Internet Protocol (IP).;Image Address Resolution ProtocolUsed to find the hardware address of a host from a known IP address; The IP address has already been given by the upper-layer protocols of the destinations IP address, so we don’t have to worry about it.If the IP (Internet Protocol) can’t find the destinations host’s hardware address in the ARP cache, it uses ARP to find this information; Often seen in duplicate IP address situations.ARP acts as a detective and interrogates the local network by sending out a broadcast asking the machine with the specified IP address to reply with its hardware address.Image of ARP
Address Resolution ProtocolUsed to find the hardware address of a host from a known IP address; The IP address has already been given by the upper-layer protocols of the destinations IP address, so we don’t have to worry about it.If the IP (Internet Protocol) can’t find the destinations host’s hardware address in the ARP cache, it uses ARP to find this information; Often seen in duplicate IP address situations.ARP acts as a detective and interrogates the local network by sending out a broadcast asking the machine with the specified IP address to reply with its hardware address.Image of ARP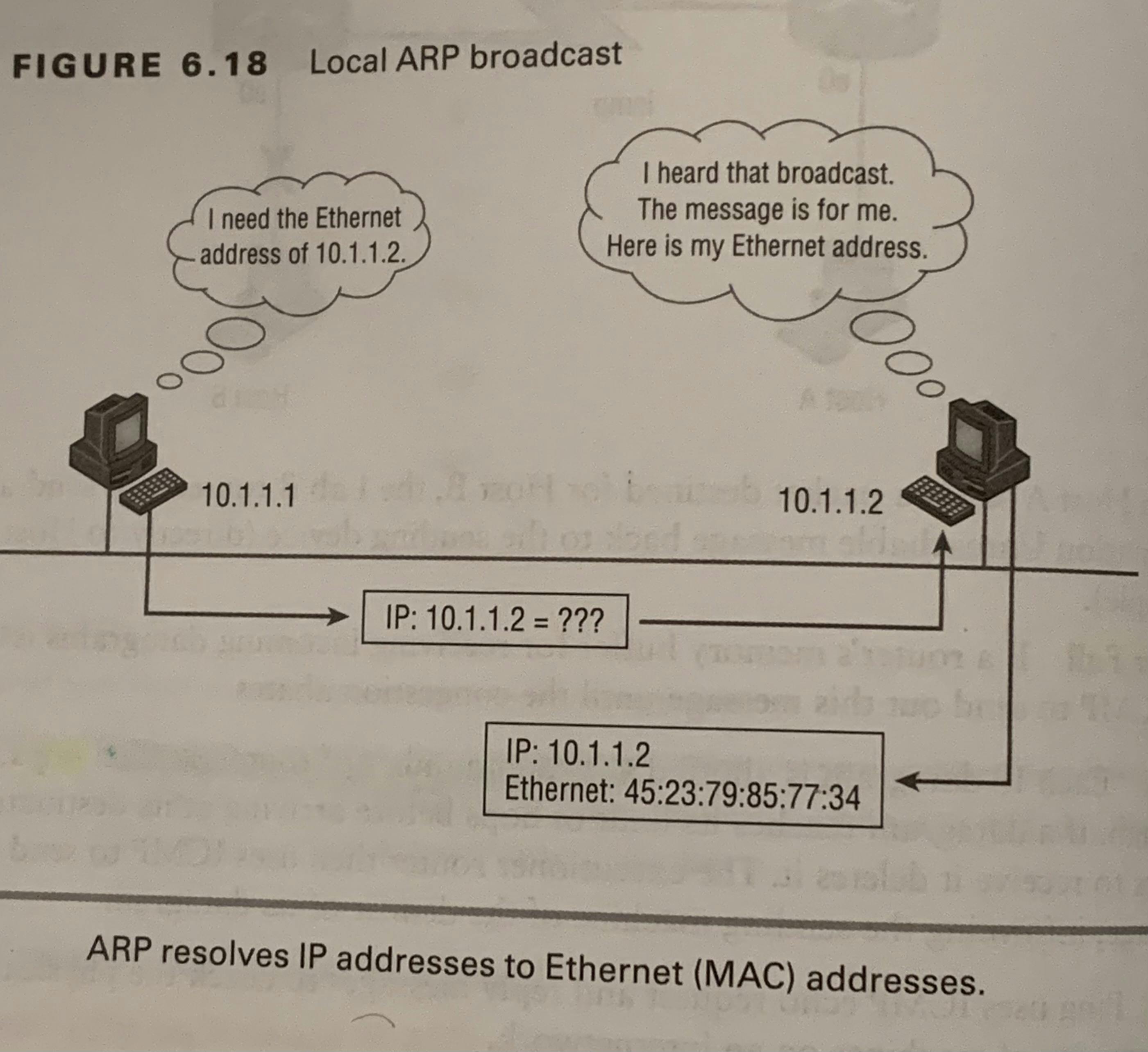 Reverse Address Resolution ProtocolThis is literally the opposite/reverse of ARP. We know our MAC address, but this time we want to know out IP address; it’s used on diskless workstations because diskless workstations don’t have a way of knowing their IP address.Image of RARP
Reverse Address Resolution ProtocolThis is literally the opposite/reverse of ARP. We know our MAC address, but this time we want to know out IP address; it’s used on diskless workstations because diskless workstations don’t have a way of knowing their IP address.Image of RARP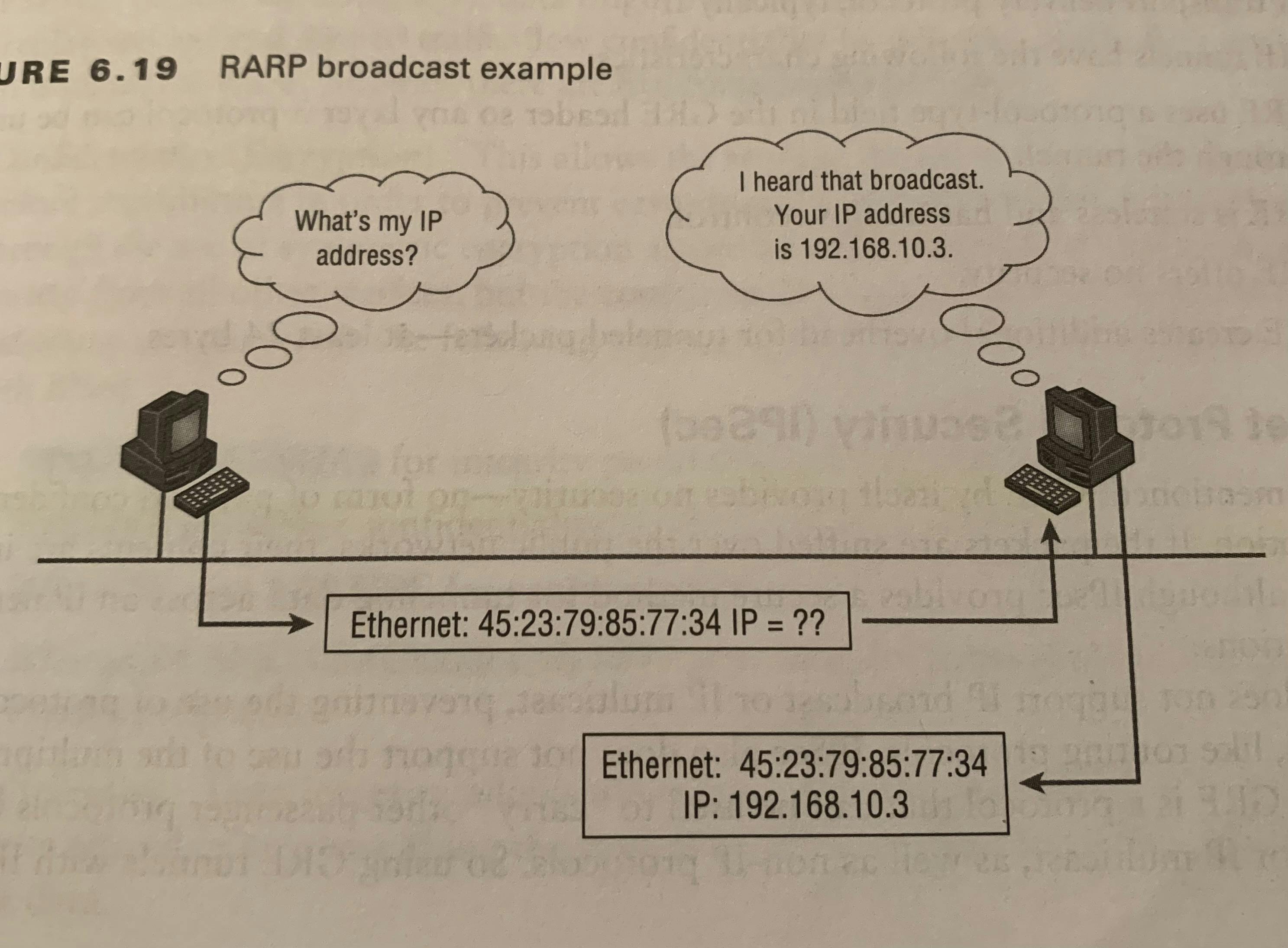 GREGeneric Routing Encapsulation (GRE) is a tunneling protocol that can encapsulate many protocols inside IP tunnels.The clear advantage of GRE over other tunneling protocols is that it can encapsulate broadcast, multicast traffic (multicast streaming or routing protocols) or other non-IP protocols.Generic routing encapsulation (GRE) tunnels are not secure because Generic routing encapsulation (GRE) does not encrypt its Data payload. In real-time, Generic routing encapsulation (GRE) used together with other secure tunneling protocols like IPSec to provide network security.Image of GRE
GREGeneric Routing Encapsulation (GRE) is a tunneling protocol that can encapsulate many protocols inside IP tunnels.The clear advantage of GRE over other tunneling protocols is that it can encapsulate broadcast, multicast traffic (multicast streaming or routing protocols) or other non-IP protocols.Generic routing encapsulation (GRE) tunnels are not secure because Generic routing encapsulation (GRE) does not encrypt its Data payload. In real-time, Generic routing encapsulation (GRE) used together with other secure tunneling protocols like IPSec to provide network security.Image of GRE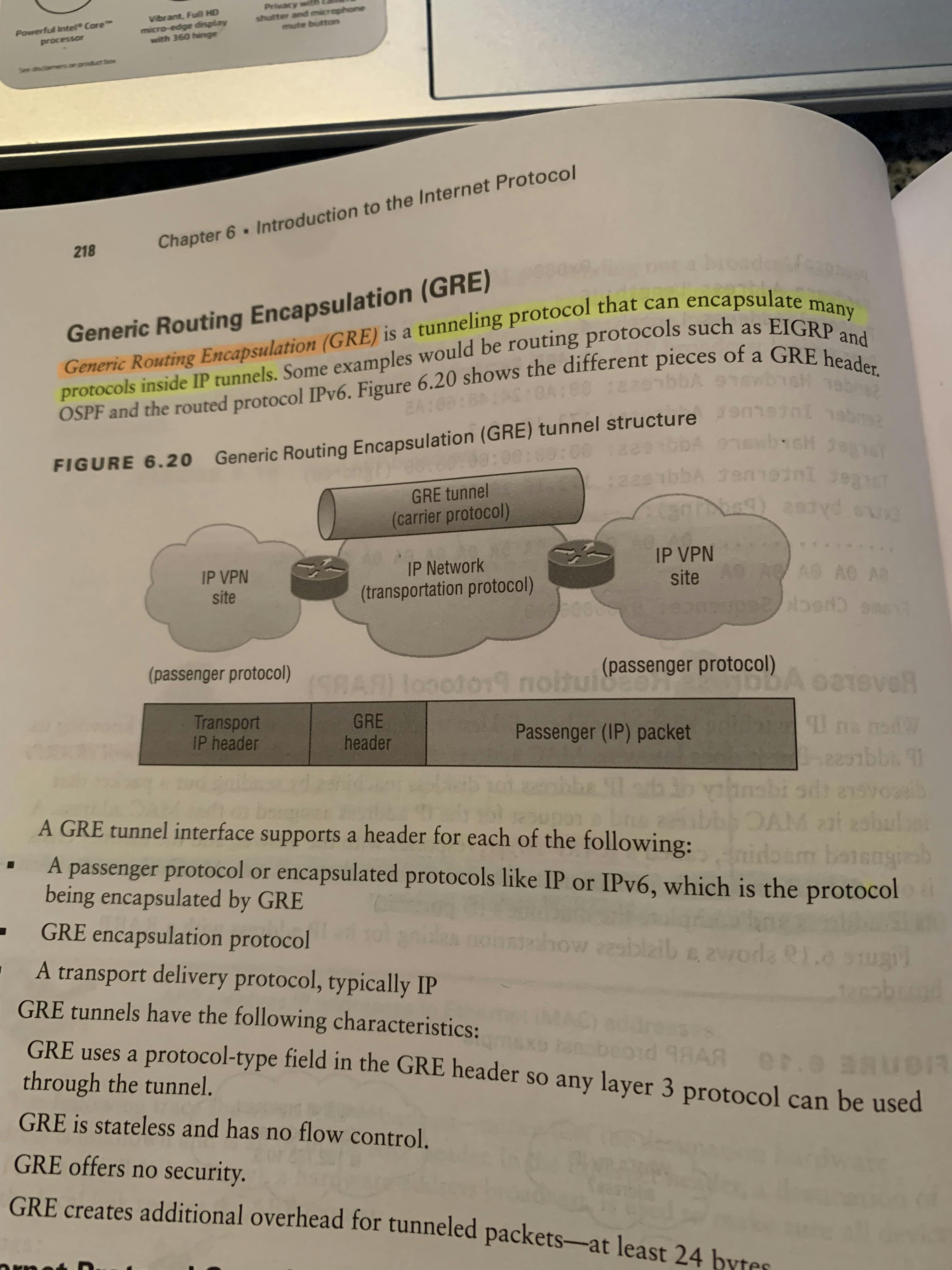 IPSecInternet Protocol Security (IPSec) provides network security to whenever GRE is used, but it does have some limitations.IPSec can’t run IP Broadcasts, IP Multicasts, or Routing Protocols on it’s own.Using GRE+IPSec allows you to run a routing protocol, IP multicast, as well as multiprotocol traffic across your network all while being encrypted. IPSec is a standards-based method of providing privacy, integrity, and authenticity to information transferred across IP networks; IPsec provides IP network-layer encryption.IPSec achieves encryption security by using two primary security protocolsAuthentication Header (AH)Authentication Header verifies origin of data and also payload to confirm if there has been modification done in between, during transmission between source and destination. The AH protocol provides a mechanism for authentication only. AH provides data integrity, data origin authentication, and an optional replay protection service.Encapsulating Security Payload (ESP)The Encapsulating Security Payload (ESP) protocol provides data confidentiality (encryption) and authentication (data integrity, data origin authentication, and replay protection). ESP can be used with confidentiality only, authentication only, or both confidentiality and authentication.AH-style authentication authenticates the entire IP packet, including the outer IP header, while the ESP-style authentication authenticates only the IP datagram portion of the IP packet.ESP > AHEncapsulation
IPSecInternet Protocol Security (IPSec) provides network security to whenever GRE is used, but it does have some limitations.IPSec can’t run IP Broadcasts, IP Multicasts, or Routing Protocols on it’s own.Using GRE+IPSec allows you to run a routing protocol, IP multicast, as well as multiprotocol traffic across your network all while being encrypted. IPSec is a standards-based method of providing privacy, integrity, and authenticity to information transferred across IP networks; IPsec provides IP network-layer encryption.IPSec achieves encryption security by using two primary security protocolsAuthentication Header (AH)Authentication Header verifies origin of data and also payload to confirm if there has been modification done in between, during transmission between source and destination. The AH protocol provides a mechanism for authentication only. AH provides data integrity, data origin authentication, and an optional replay protection service.Encapsulating Security Payload (ESP)The Encapsulating Security Payload (ESP) protocol provides data confidentiality (encryption) and authentication (data integrity, data origin authentication, and replay protection). ESP can be used with confidentiality only, authentication only, or both confidentiality and authentication.AH-style authentication authenticates the entire IP packet, including the outer IP header, while the ESP-style authentication authenticates only the IP datagram portion of the IP packet.ESP > AHEncapsulation
Application/Service ProtocolsFile Transfer Protocol (FTP) (TCP 20,21)File Transfer Protocol (FTP)(TCP 20,21) refers to a group of rules that govern how computers transfer files from one system to another over the internet over an IP network. Businesses use FTP to send files between computers, while websites use FTP for the uploading and downloading of files from their website's servers.One of the main reasons why modern businesses and individuals need FTP is its ability to perform large file size transfers. When sending a relatively small file, like a Word document, most methods will do, but with FTP, you can send hundreds of gigabytes at once and still get a smooth transmission.Image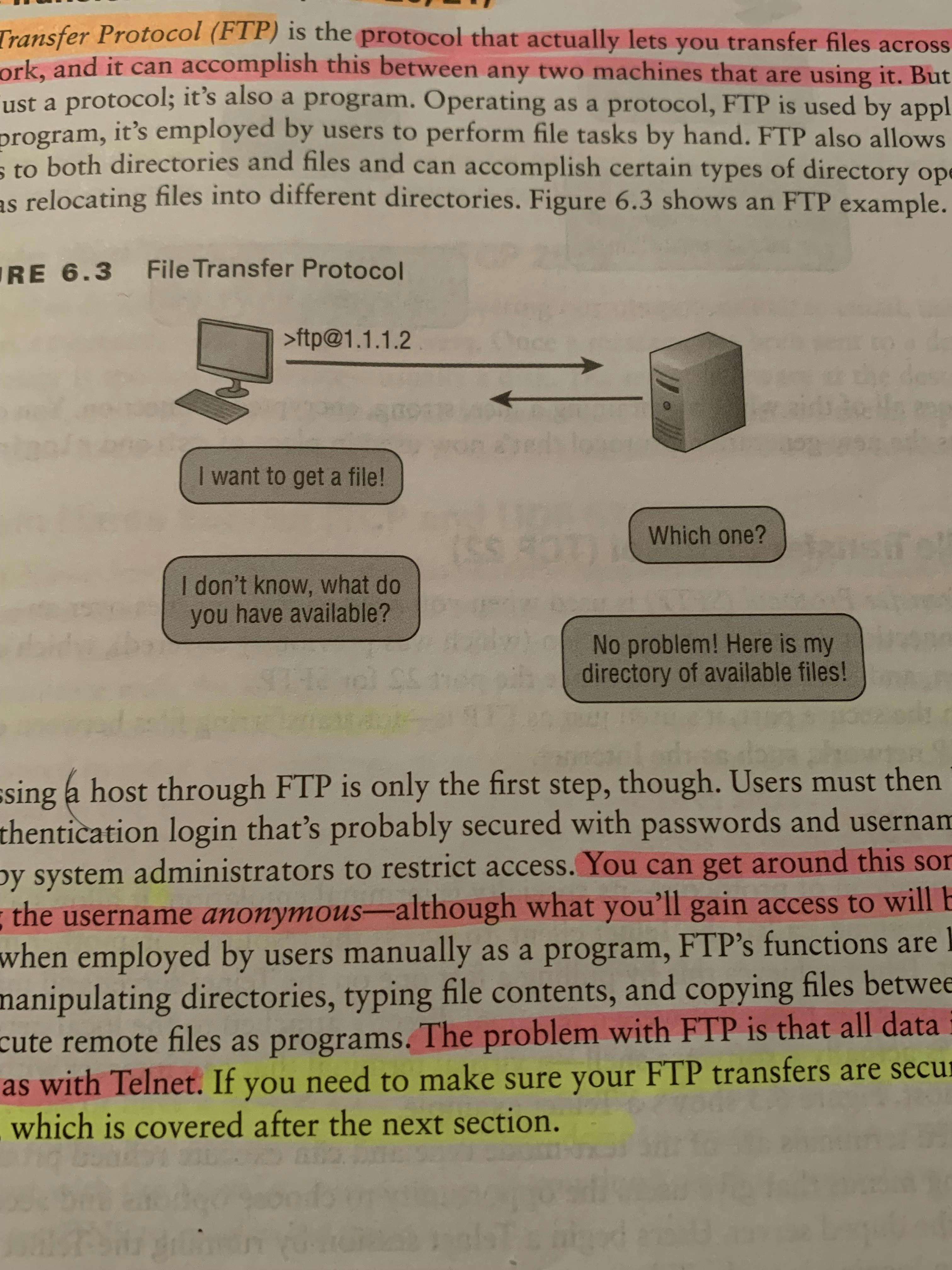 SSH (TCP 22)Secure Shell (SSH)(TCP 22) protocol sets up a secure Telnet session over a standard TCP/IP connection and is employed for doing things like logging into other systems, running programs on remote systems, and moving files from one system to another.And it does all of this while maintaining a nice, strong, encrypted connection.Image
SSH (TCP 22)Secure Shell (SSH)(TCP 22) protocol sets up a secure Telnet session over a standard TCP/IP connection and is employed for doing things like logging into other systems, running programs on remote systems, and moving files from one system to another.And it does all of this while maintaining a nice, strong, encrypted connection.Image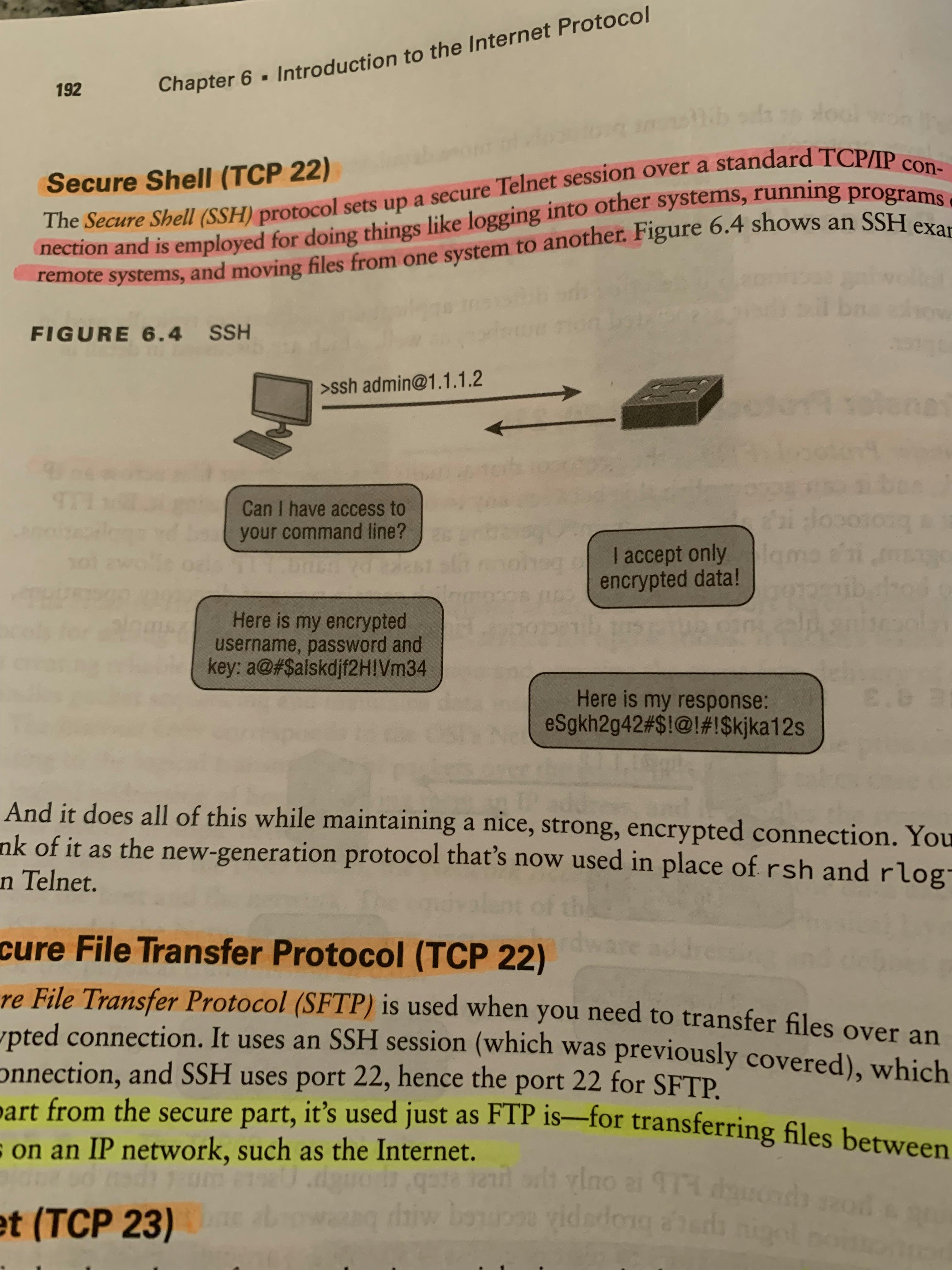 Security File Transfer Protocol (TCP 22)Security File Transfer Protocol (SFTP)(TCP 22) is used when you need to transfer files over an encrypted connection. It does this by using an SSH session, which encrypts the connection.Telnet (TCP 23)Telnet (TCP 23) allows a user on a remote client machine, called the Telnet machine, to access the resources of another machine, the Telnet Server.Telnet does it this by making it appear as though it were a terminal directly attached to the local network of the command line of the machine it’s trying to access.Telnet offers no security or encryption and is replaced by Secure Shell (SSH) when security is needed.SMTP (TCP 25)Simple Mail Transfer Protocol (SMTP) (TCP 25) uses a spooled, or queue method of mail delivery; Once a message has been sent to a destination, the message is put into a queue on a device —usually on the disk.The server software of the destination checks the queue for email messages; When it detects them, it proceeds to deliver them to their destination.SMTP is used to send mail, while POP3 is used to receive mail.Operates at the Application Level (7) of the OSI model.DNS (TCP and UDP 53)Domain Name Service (DNS)(UDP53) maps IP addresses to internet names or URLs; DNS allows you to map a domain name to a specific IP address.Because of this, you can change the IP address as often as you want and no one will know the difference because it’s mapped to a Domain name; This means the IP address can change, but the domain name will stay the same.Fully Qualified Domain Name (FQDN) is a hierarchy that can logically locate a system based on its domain identifier.Ex. In this example, the “www” is the hostname, “networksolutions” is the second-level domain and “com” is the TLD. Each label is separated by a period and the final period is what we refer to as the “trailing period.”DNS uses UDP + TCPImage of DNS in Action!
Security File Transfer Protocol (TCP 22)Security File Transfer Protocol (SFTP)(TCP 22) is used when you need to transfer files over an encrypted connection. It does this by using an SSH session, which encrypts the connection.Telnet (TCP 23)Telnet (TCP 23) allows a user on a remote client machine, called the Telnet machine, to access the resources of another machine, the Telnet Server.Telnet does it this by making it appear as though it were a terminal directly attached to the local network of the command line of the machine it’s trying to access.Telnet offers no security or encryption and is replaced by Secure Shell (SSH) when security is needed.SMTP (TCP 25)Simple Mail Transfer Protocol (SMTP) (TCP 25) uses a spooled, or queue method of mail delivery; Once a message has been sent to a destination, the message is put into a queue on a device —usually on the disk.The server software of the destination checks the queue for email messages; When it detects them, it proceeds to deliver them to their destination.SMTP is used to send mail, while POP3 is used to receive mail.Operates at the Application Level (7) of the OSI model.DNS (TCP and UDP 53)Domain Name Service (DNS)(UDP53) maps IP addresses to internet names or URLs; DNS allows you to map a domain name to a specific IP address.Because of this, you can change the IP address as often as you want and no one will know the difference because it’s mapped to a Domain name; This means the IP address can change, but the domain name will stay the same.Fully Qualified Domain Name (FQDN) is a hierarchy that can logically locate a system based on its domain identifier.Ex. In this example, the “www” is the hostname, “networksolutions” is the second-level domain and “com” is the TLD. Each label is separated by a period and the final period is what we refer to as the “trailing period.”DNS uses UDP + TCPImage of DNS in Action!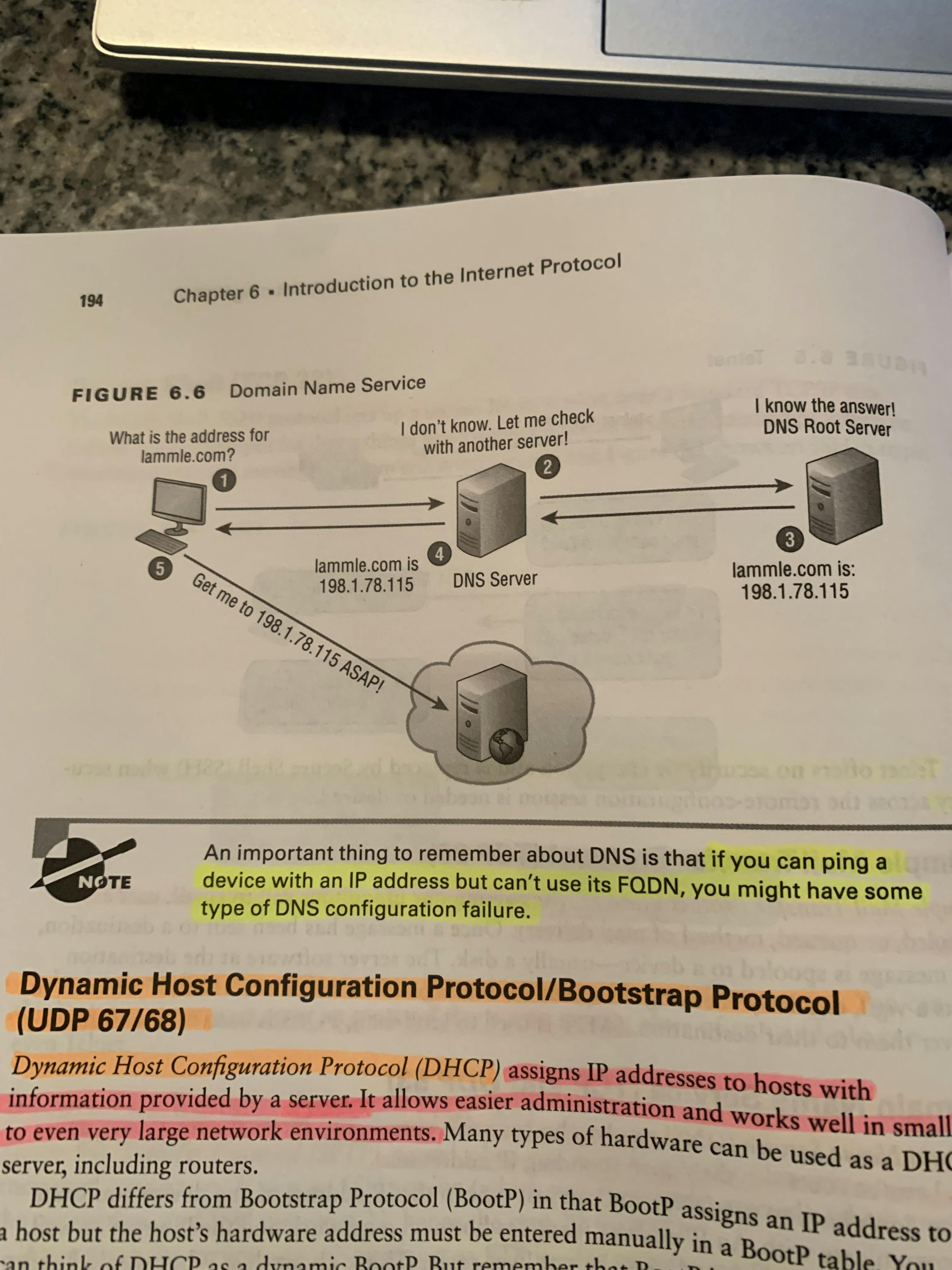 DHCP (UDP 67/68)Dynamic Host Configuration Protocol (DHCP)(UDP 67/68) assigns IP addresses to hosts with information provided by a server. It allows easier administration and works well in a small to even very large network environment. DHCP can provide the following:IP Address, Subnet Mask, Domain Name, Default Gateway, DNS, Windows Internet Naming Service (WINS) information.A client that sends out a DHCP Discover message in order to receive an IP address sends out a broadcast at both layer 2 and layer 3; The Layer 2 Broadcast is all Fs in hexadecimal, which looks like this: FF:FF:FF:FF:FF:FF. The Layer 3 Broadcasts is 255.255.255.255 which is all networks and hosts.The Data Link and Network layers are both sending out “all hands on deck” broadcasts saying, “Help! Idk my IP address!”Below is the Four-Step Process a client takes to receive an IP address from a DHCP server:Discover. DHCP Client (Host) broadcasts a DHCP Discover Message looking for a DHCP Server (port 67)Offer. DHCP server that received the DHCP Discover message sends a unicast (direct) DHCP Offer message back to the host.Request. DHCP client then broadcasts to the server a DHCP request message asking for the offered IP address and possibly other information.Accept. The server finalizes the exchange with a unicast (direct) DHCP acknowledgement message.Image of DORA
DHCP (UDP 67/68)Dynamic Host Configuration Protocol (DHCP)(UDP 67/68) assigns IP addresses to hosts with information provided by a server. It allows easier administration and works well in a small to even very large network environment. DHCP can provide the following:IP Address, Subnet Mask, Domain Name, Default Gateway, DNS, Windows Internet Naming Service (WINS) information.A client that sends out a DHCP Discover message in order to receive an IP address sends out a broadcast at both layer 2 and layer 3; The Layer 2 Broadcast is all Fs in hexadecimal, which looks like this: FF:FF:FF:FF:FF:FF. The Layer 3 Broadcasts is 255.255.255.255 which is all networks and hosts.The Data Link and Network layers are both sending out “all hands on deck” broadcasts saying, “Help! Idk my IP address!”Below is the Four-Step Process a client takes to receive an IP address from a DHCP server:Discover. DHCP Client (Host) broadcasts a DHCP Discover Message looking for a DHCP Server (port 67)Offer. DHCP server that received the DHCP Discover message sends a unicast (direct) DHCP Offer message back to the host.Request. DHCP client then broadcasts to the server a DHCP request message asking for the offered IP address and possibly other information.Accept. The server finalizes the exchange with a unicast (direct) DHCP acknowledgement message.Image of DORA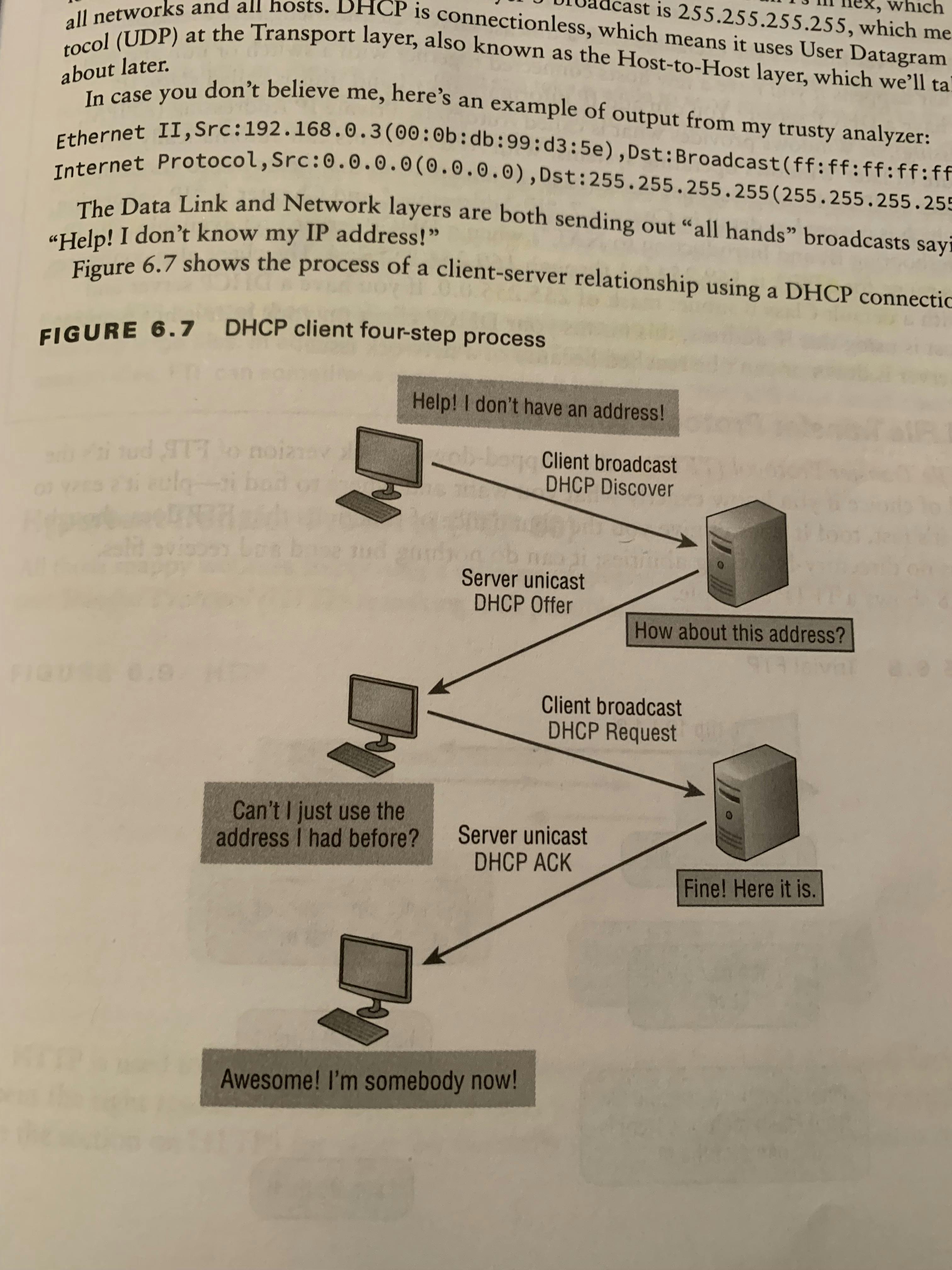 TFTP (UDP 69)Trivial File Transfer Protocol (UDP 69) is the stripped down version, stock, very basic version of FTP, but it’s the protocol of choice if you know exactly what you want where to find it — plus it’s real fast and easy to use! It just doesn’t give the same large amount of functions as FTP does; It can do nothing but send and receive files. It also can send only small amounts of data with zero authentication, making it very insecure. Image of TFTP in Action!
TFTP (UDP 69)Trivial File Transfer Protocol (UDP 69) is the stripped down version, stock, very basic version of FTP, but it’s the protocol of choice if you know exactly what you want where to find it — plus it’s real fast and easy to use! It just doesn’t give the same large amount of functions as FTP does; It can do nothing but send and receive files. It also can send only small amounts of data with zero authentication, making it very insecure. Image of TFTP in Action!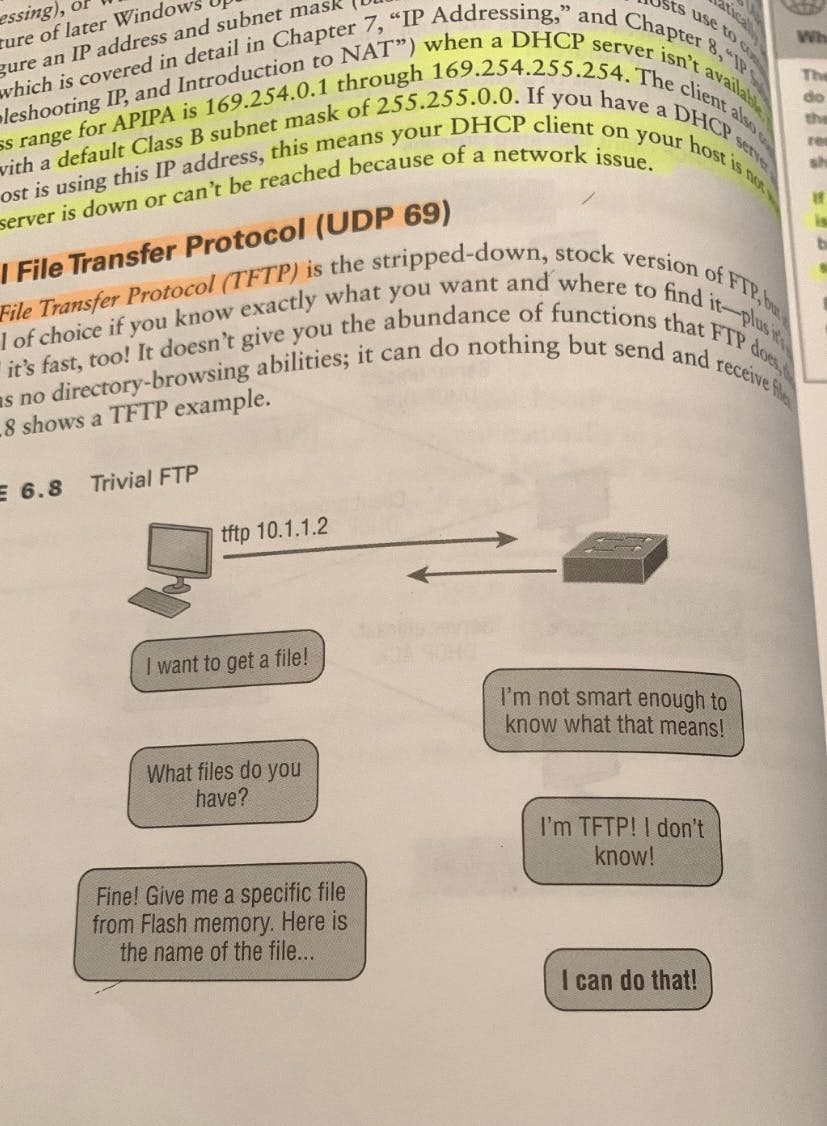 HTTP (TCP 80)Hypertext Transfer Protocol (TCP 80) is used to manage communications between web browsers and web servers, and it opens the right resources when you click a link, wherever that resource may actually reside.Image of HTTP in Action
HTTP (TCP 80)Hypertext Transfer Protocol (TCP 80) is used to manage communications between web browsers and web servers, and it opens the right resources when you click a link, wherever that resource may actually reside.Image of HTTP in Action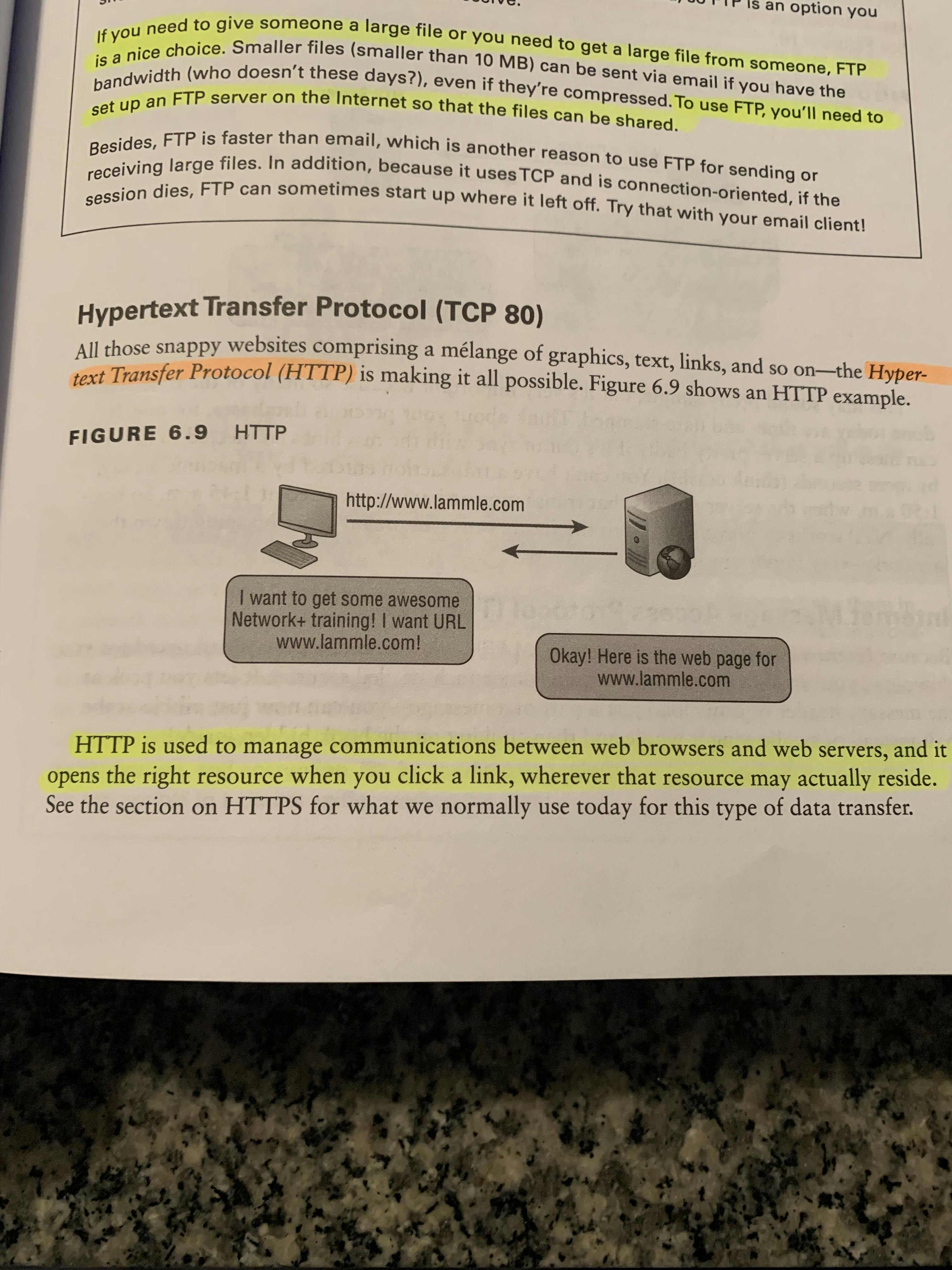 POP3 (TCP 110)Post Office Protocol v3 (TCP 110) gives us a storage facility for incoming mail; Basically this protocol works when a client device connects to a POP3 server and messages addressed to that client are released for downloading.It only downloads email from a email server and only downloads what’s in your inbox folder (doesn’t download the sent, outbox, or draft)POP3 Doesn’t synchronize the mail across multiple devices. Ex. If you’re logged-in onto a laptop & a Tablet, POP3 will only send copy of the email to one of your devices and once it’s delivered, that’s it. Since synchronization is absent, you can be logged into two devices with your email and still have a different inboxes and folder structures across both devices.It doesn’t allow messages to be downloaded selectively, but once they are, the client server interaction ends and you can locally delete and tweak your messages. It allows for Basic Mail transfer functionality.Image of POP3
POP3 (TCP 110)Post Office Protocol v3 (TCP 110) gives us a storage facility for incoming mail; Basically this protocol works when a client device connects to a POP3 server and messages addressed to that client are released for downloading.It only downloads email from a email server and only downloads what’s in your inbox folder (doesn’t download the sent, outbox, or draft)POP3 Doesn’t synchronize the mail across multiple devices. Ex. If you’re logged-in onto a laptop & a Tablet, POP3 will only send copy of the email to one of your devices and once it’s delivered, that’s it. Since synchronization is absent, you can be logged into two devices with your email and still have a different inboxes and folder structures across both devices.It doesn’t allow messages to be downloaded selectively, but once they are, the client server interaction ends and you can locally delete and tweak your messages. It allows for Basic Mail transfer functionality.Image of POP3 NTP (UDP 123)Network Time Protocol (NTP)(UDP 123) is used to synchronize the clocks on our computers to one standard time source, typically an atomic clock.NTP ensures that all computers on a given network agree on the time.IMAP (TCP 143)Internet Message Access Protocol (IMAP TCP 143) allows you to view your email across multiple devices, it stores local cache copies on any device your email is signed into. It does this by stores the email on a mail server.Because all of the email is stored on a mail server, this allows any device with an internet connection to access your emails; All the emails and folder structures are synchronized. One change on one device is synced with the email of your other device; You can see all your email including sent items, drafts, deleted items, and any custom folders.Image of IMAP143
NTP (UDP 123)Network Time Protocol (NTP)(UDP 123) is used to synchronize the clocks on our computers to one standard time source, typically an atomic clock.NTP ensures that all computers on a given network agree on the time.IMAP (TCP 143)Internet Message Access Protocol (IMAP TCP 143) allows you to view your email across multiple devices, it stores local cache copies on any device your email is signed into. It does this by stores the email on a mail server.Because all of the email is stored on a mail server, this allows any device with an internet connection to access your emails; All the emails and folder structures are synchronized. One change on one device is synced with the email of your other device; You can see all your email including sent items, drafts, deleted items, and any custom folders.Image of IMAP143 SNMP (TCP or UDP 161/162)Simple Network Management Protocol (SNMP UDP 161/162) collects and manipulates valuable network information. It gathers data by polling the devices on the network from a management station at fixed or random intervals, requiring them to disclose certain information.The goal of all this is to create a baseline for the network; Baseline refers to what is considered to be normal for the network, it’s a report delimiting the operational traits of a healthy network.This protocol can also stand as a watchdog over the network, quickly notifying managers of any sudden big changes to the network.Agents are the so-called “watch dogs”. Whenever the network deviates from the baseline, these agents send an alert called a “Trap” to the management station. The management station then checks the MIB (Management Information Base); The MIB is a database of predefined questions the NMS (Network Management System) can ask the agents regarding the health of the network.Image of SNMP in Action
SNMP (TCP or UDP 161/162)Simple Network Management Protocol (SNMP UDP 161/162) collects and manipulates valuable network information. It gathers data by polling the devices on the network from a management station at fixed or random intervals, requiring them to disclose certain information.The goal of all this is to create a baseline for the network; Baseline refers to what is considered to be normal for the network, it’s a report delimiting the operational traits of a healthy network.This protocol can also stand as a watchdog over the network, quickly notifying managers of any sudden big changes to the network.Agents are the so-called “watch dogs”. Whenever the network deviates from the baseline, these agents send an alert called a “Trap” to the management station. The management station then checks the MIB (Management Information Base); The MIB is a database of predefined questions the NMS (Network Management System) can ask the agents regarding the health of the network.Image of SNMP in Action LDAP (TCP 389)Lightweight Directory Access Protocol (LDAP TCP 389) is used to access the network directory that contains all of your network resources, such as devices, users, and active directory.LDAPS (TCP 636) is the secure version of LDAPImage of LDAP
LDAP (TCP 389)Lightweight Directory Access Protocol (LDAP TCP 389) is used to access the network directory that contains all of your network resources, such as devices, users, and active directory.LDAPS (TCP 636) is the secure version of LDAPImage of LDAP HTTPS (TCP 443)Hypertext Transfer Protocol (TCP 443) Secure is the secure version of HTTP that gives you a bunch of security tools for keeping transactions secure between a web browser and a server.It’s what your browser needs to fill out forms, sign in, authenticate and encrypt an HTTP message when you make a reservation or buy something online.TLS (TCP 995/465)Transport Layer Security (TCP 995/465) is a a widely adopted security protocol designed to facilitate privacy and data security for communications over the Internet. A primary use case of TLS is encrypting the communication between web applications and servers, such as web browsers loading a website. SMB (TCP 445)Server Message Block (SMB TCP 445) is used for sharing access to files and printers and other communications between hosts on a Microsoft Windows Network.Image of SMB
HTTPS (TCP 443)Hypertext Transfer Protocol (TCP 443) Secure is the secure version of HTTP that gives you a bunch of security tools for keeping transactions secure between a web browser and a server.It’s what your browser needs to fill out forms, sign in, authenticate and encrypt an HTTP message when you make a reservation or buy something online.TLS (TCP 995/465)Transport Layer Security (TCP 995/465) is a a widely adopted security protocol designed to facilitate privacy and data security for communications over the Internet. A primary use case of TLS is encrypting the communication between web applications and servers, such as web browsers loading a website. SMB (TCP 445)Server Message Block (SMB TCP 445) is used for sharing access to files and printers and other communications between hosts on a Microsoft Windows Network.Image of SMB Syslog (UDP 514)Syslog allows you to display, sort, and even search messages from a switch or router’s internal buffer; it’s used to see exactly what’s going on with your network so you can effectively troubleshoot it.Network devices can be configured to generate a syslog message and forward it to various destinations; These messages can be categorized by severity level as well.Image
Syslog (UDP 514)Syslog allows you to display, sort, and even search messages from a switch or router’s internal buffer; it’s used to see exactly what’s going on with your network so you can effectively troubleshoot it.Network devices can be configured to generate a syslog message and forward it to various destinations; These messages can be categorized by severity level as well.Image SMTP TLS (TCP 587)SMTP TLS (TCP 587) encrypts email when it is sent, and most email servers use or can use port 587 to send email now; This protocol coupled with TL encryption, will ensure that email is securely sent.SMTP is used to send email and email scans using a spooled or queue method of delivering email over TCP port 25.LDAP SSL (TCP 636)LDAP SSL (TCP 636) is used to access the network directory that contain all of your network resources, such as devices, users, and active directory over a secure connection.IMAP SSL (TCP 993)IMAP SSL (TCP 993) allows IMAP traffic to travel over a secure connection.POP3 SSL (TCP 995)POP3 SSL is (TCP 995) is the secure version of POP3, a email protocol that only sends one local copy of an email to the first device that asks for it.SQL (TCP 1433)Structured Language Query (SQL)(TCP 1433) is the port number for Microsoft’s SQL Server that is a multipurpose enterprise-level data platform.SQLnet (TCP 1521)SQLnet (TCP 1521) is Oracle’s networking software that allows remote data access between programs using Oracles Databases; Applications and Databases are shared with different machines and continue to communicate as if they are localMySQL (TCP 3306)MySQL (TCP 3306) is a relational database management system based on Structured Query Language (SQL). Used for companies for data warehousing, e-commerce, logging applications, and more; The most common use for MySQL is for the purpose of a cloud-based database.RDP (TCP 3389)Remote Desktop Protocol (RDP)(TCP 3389) is a proprietary protocol developed by Microsoft. It allows you to connect to another windows computer and run programs.SIP (TCP/UDP 5060 and 5061)Session Initiation Protocol (SIP) is a very popular signaling protocol used to construct and deconstruct multimedia communication session for many things like voice and video call, videoconferencing, streaming multimedia sessions, instant messaging, presence information, and online games over the internet. Image of SIP
SMTP TLS (TCP 587)SMTP TLS (TCP 587) encrypts email when it is sent, and most email servers use or can use port 587 to send email now; This protocol coupled with TL encryption, will ensure that email is securely sent.SMTP is used to send email and email scans using a spooled or queue method of delivering email over TCP port 25.LDAP SSL (TCP 636)LDAP SSL (TCP 636) is used to access the network directory that contain all of your network resources, such as devices, users, and active directory over a secure connection.IMAP SSL (TCP 993)IMAP SSL (TCP 993) allows IMAP traffic to travel over a secure connection.POP3 SSL (TCP 995)POP3 SSL is (TCP 995) is the secure version of POP3, a email protocol that only sends one local copy of an email to the first device that asks for it.SQL (TCP 1433)Structured Language Query (SQL)(TCP 1433) is the port number for Microsoft’s SQL Server that is a multipurpose enterprise-level data platform.SQLnet (TCP 1521)SQLnet (TCP 1521) is Oracle’s networking software that allows remote data access between programs using Oracles Databases; Applications and Databases are shared with different machines and continue to communicate as if they are localMySQL (TCP 3306)MySQL (TCP 3306) is a relational database management system based on Structured Query Language (SQL). Used for companies for data warehousing, e-commerce, logging applications, and more; The most common use for MySQL is for the purpose of a cloud-based database.RDP (TCP 3389)Remote Desktop Protocol (RDP)(TCP 3389) is a proprietary protocol developed by Microsoft. It allows you to connect to another windows computer and run programs.SIP (TCP/UDP 5060 and 5061)Session Initiation Protocol (SIP) is a very popular signaling protocol used to construct and deconstruct multimedia communication session for many things like voice and video call, videoconferencing, streaming multimedia sessions, instant messaging, presence information, and online games over the internet. Image of SIP RTP (UDP 5004/ TCP 5005)Real-Time Transport Protocol (SIP)(UDP 5004)(TCP 5005) is a packet-formatting method for delivering audio and video over the Internet.Used for streaming media, video conferencing, and push-to-talk systems — basically making it the standard for Voice over IP (VoIP).MGCP (TCP 2427/2727)MGCP stands for Media Gateway Control Protocol (TCP 2427/2727). It is a protocol that is extensively used for signalling and controlling communications protocols applied in VoIP telecommunication systems. H.323 (TCP 1720)H.323 (TCP 1720) is a protocol that provides a standard for video on an IP network that defines how real-time audio, video, and data information is transmitted. This provides signaling, multimedia, and bandwidth control mechanisms.IGMPInternet Group Management Protocol (IGMP) is the TCP/IP protocol used for managing IP multicast sessions. IGMP messages come in handy for tracking group memberships as well as active multicast streams; IGMP works at the Network layer and doesn’t use port numbers.NetBIOS (TCP and UDP 137-139)Network Basic/Input/Output/System (TCP + UDP 137-139) allows computers and applications to communicate with network hardware, and allows data to transmit properly over a network
RTP (UDP 5004/ TCP 5005)Real-Time Transport Protocol (SIP)(UDP 5004)(TCP 5005) is a packet-formatting method for delivering audio and video over the Internet.Used for streaming media, video conferencing, and push-to-talk systems — basically making it the standard for Voice over IP (VoIP).MGCP (TCP 2427/2727)MGCP stands for Media Gateway Control Protocol (TCP 2427/2727). It is a protocol that is extensively used for signalling and controlling communications protocols applied in VoIP telecommunication systems. H.323 (TCP 1720)H.323 (TCP 1720) is a protocol that provides a standard for video on an IP network that defines how real-time audio, video, and data information is transmitted. This provides signaling, multimedia, and bandwidth control mechanisms.IGMPInternet Group Management Protocol (IGMP) is the TCP/IP protocol used for managing IP multicast sessions. IGMP messages come in handy for tracking group memberships as well as active multicast streams; IGMP works at the Network layer and doesn’t use port numbers.NetBIOS (TCP and UDP 137-139)Network Basic/Input/Output/System (TCP + UDP 137-139) allows computers and applications to communicate with network hardware, and allows data to transmit properly over a network

 1.5 Explain common ports and protocols, their application, and encrypted alternatives.
1.5 Explain common ports and protocols, their application, and encrypted alternatives.
Last edited 940 days ago by Makiel [Muh-Keel].
Analogy of how IP works
Before anything, always remember that the Internet Layer is just IP (Internet Protocol). All the other layers exist just to support it. IP holds the big picture and can see it all in that it’s aware of all the interconnected networks.






Protocols at the Internet Layer
Before anything, always remember that the Internet Layer is just IP (Internet Protocol). All the other layers exist just to support it. IP holds the big picture and can see it all in that it’s aware of all the interconnected networks.




Protocols and their Port Numbers













Want to print your doc?
This is not the way.
This is not the way.

Try clicking the ··· in the right corner or using a keyboard shortcut (
CtrlP
) instead.