Chapter: 08. Online Surfing And Cyber Security
One Touch Learn
A. Tick (✓) the correct option.
____ is not a cloud storage. The technique of watching the person while talking to him is called ____ is not a communication service of the Internet. ____ is used to store and manage data on a remote server in place of their local computer. The process of stealing personal information, changing financial data, and breaking security systems to gain unauthorised access to computer systems is called B. Write ‘T’ for true and ‘F’ for false.
Avoid using pirated copies of software. Facebook is an example of an e-mail service provider. No one keeps a check on the comments of participants on the newsgroup. Cyber threat is a criminal activity in which computers are used to damage data, steal data, or disrupt digital life of a person. Chatting refers to a communication in the form of small messages among the computers over the Internet. C. Fill in the blanks using the words given below:
Carding refers to the process of stealing credit card numbers online. An E-greeting is just like a paper greeting card. Chat is a conversation that takes place in a friendly atmosphere. The process of protecting computer resources such as networks, devices, programs, and data from unauthorised access, damage, or attack is called cyber security. Let’s Do It
A. Short answer type questions.
Phreaking is a crime committed against telephone companies by using computers with the goal of making free long-distance calls, impersonating directory assistance or other operator services, diverting calls to numbers of the perpetrator’s choice, or tapping phone lines. A newsgroup is an online discussion group where people talk about a specific topic, with all participants sharing their thoughts and ideas. It is generally managed by a News Admin who approves comments and views. Is the use of social networking services advisable for students? Why or Why not? No, the use of social networking services is generally not advisable for students as they are considered a significant source of distraction from education. Cloud storage is a service where users are able to store and manage their data on a remote server instead of their local computer. This allows them to access their data from anywhere in the world by logging into their cloud storage account. B. Long answer type questions.
Write any four safety measures while using the Internet. Never provide personal information, such as your address, phone number, or school name or location. Always keep your browser’s privacy settings ON to protect your online activities. Use the Internet only in the presence of your elders (parents or guardians) for supervision. Do not share your passwords with anyone, other than your parents or teachers if absolutely necessary for legitimate reasons. Never agree to meet anyone you’ve met online in person without your parents’ explicit permission and supervision. Never respond to an unknown e-mail, message, post, or text, as they could be phishing attempts or scams. Discuss different ways of communication through Internet. E-mail: Allows sending electronic messages and files quickly to individuals or multiple recipients worldwide. Video Conferencing: Enables face-to-face communication over the Internet, allowing two or more people in different locations to talk and see each other simultaneously, useful for business, education, and medicine. Voice-over-Internet Protocol (VoIP): Provides calling facilities over the Internet, allowing transfer of voice, fax, and multimedia content using various devices, often with free VoIP-to-VoIP calls. Chatting: Refers to real-time communication through small text messages over the Internet, which can be one-to-one or one-to-many. Social Networking: Platforms where people with common interests can connect, share views, ideas, and various forms of media like audio, video, and images. Newsgroup: Online discussion groups focused on specific topics, where participants share comments and views on the topic and each other’s contributions. E-Greetings: Digital greeting cards created with text and effects, sent via email, offering a paper-saving and engaging alternative to traditional cards. What is the difference between hacking and cracking? Hacking is the act of accessing someone else’s computer or account without permission. Hackers might steal information, modify data, or cause other problems. However, some organizations employ ethical hackers to identify and fix security flaws in their own systems to prevent malicious attacks. Cracking is a more malicious process that involves specifically stealing personal information, changing financial data, and breaking security systems to gain unauthorized access to computer systems, typically for criminal intent. Software obtained through cracking is considered illegal and is known as pirated software. Define the types of cyber threats. Data Diddling: This cyber threat involves changing the data that is either entering or exiting a computer system, often to manipulate records or information for personal gain. Phreaking: This criminal activity is directed against telephone companies, utilizing computers to achieve goals such as making free long-distance calls, impersonating operator services, redirecting calls, or tapping phone lines. Cloning: This fraud involves using scanners to illicitly obtain the electronic serial numbers of cellular phones. These stolen serial numbers are then used to create cloned phones, allowing the perpetrator to make free calls that are charged to the original phone’s legitimate owner. Carding: This refers to the crime of stealing credit card numbers online. Once stolen, these numbers are either resold to others or used by the perpetrator to make unauthorized purchases of merchandise against the victim’s account. Hacking: This is the unauthorized access to another person’s computer system or account, which may lead to theft of information, alteration of data, or disruption of services. Cracking: This process involves deliberately breaking security systems to gain unauthorized access to computer systems, often with the intent to steal personal information or change financial data. C. Application-based questions.
Arun, a software engineer in Gurugram, needs to transfer money urgently to his parents in Varanasi because his mother is hospitalised. He’s unsure which money transfer option is best for this urgent situation. What are some good options and reasons for using them? A good option for Arun would be to use E-banking services such as online fund transfer (e.g., NEFT, IMPS, or UPI) through his bank’s mobile app or website. Reasons for using E-banking: Urgency: E-banking allows for near-instant or same-day fund transfers (especially IMPS/UPI), which is critical in a medical emergency. Convenience: Transfers can be initiated from anywhere at any time (24/7) using a computer or smartphone, eliminating the need to visit a bank branch. Efficiency: It avoids the delays associated with traditional methods like cheques, which can take days to clear. Security: Online banking platforms use encryption and security protocols to ensure safe transactions. Nishant, needing to submit his science project after the deadline, uses his father’s logged-in email without permission to send it to his teacher. Was this the right action? If not, what is an alternative solution? No, this was not the right action. Using someone else’s email account without their explicit permission is a breach of privacy and trust, and it goes against proper online etiquette (netiquettes). Alternative Solution: Nishant should have informed his father about the situation and asked for his permission to use the email or, even better, requested his father to send the email on his behalf. Ideally, Nishant should have communicated with his teacher directly from his own email account, explaining the situation honestly and requesting an extension or permission to submit the project late. Higher Order Thinking Skills (HOTS)
Why should you never meet with someone you met online without your parents’ permission and/or supervision? Write some of the potential risks and safety concerns associated with online meetings. You should never meet someone you met online without your parents’ permission and/or supervision because people online might not be who they claim to be. They could be much older, have harmful intentions, or be trying to deceive you. Potential Risks and Safety Concerns: Identity Misrepresentation: The person might lie about their age, gender, identity, or intentions, posing a threat to your safety. Predatory Behavior: There’s a risk of encountering individuals who intend to harm, exploit, or abuse you physically or emotionally. Kidnapping/Physical Harm: In extreme cases, meeting an online stranger can lead to dangerous situations like kidnapping or physical assault. Theft or Extortion: You could be tricked into giving away personal information or belongings, or even become a victim of extortion. Emotional Distress: Even if not physically harmed, the encounter could be frightening or emotionally traumatic. Lack of Accountability: If something goes wrong, it can be very difficult to track down or hold the person accountable. You saw your brother writing a mail to his teacher in all capital letter while submitting his project work. You told him to not to use all capital letters. He asked you why. What will you answer him? I would tell him that typing in all capital letters in an email is considered to be like “shouting” or yelling at the person you are communicating with online. It’s a rule of netiquette (network etiquette) to avoid using all caps for regular text because it comes across as aggressive, rude, or demanding. Also, text written in all capital letters is generally harder to read, and for a formal communication like submitting project work to a teacher, it’s important to maintain a respectful and polite tone. Crack The Code
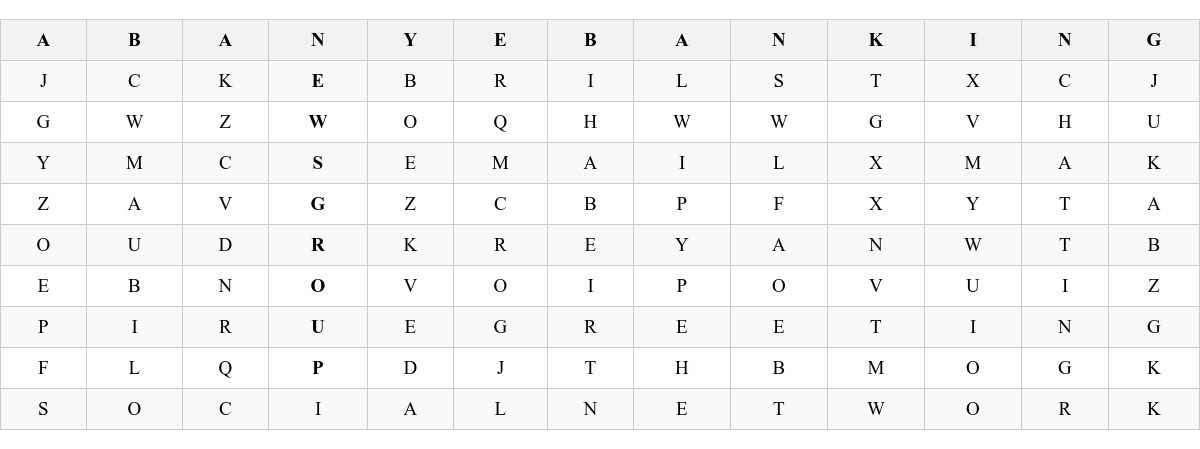
The names of six Internet services found in the grid are:
EBANKING (Horizontal, Row 1) EMAIL (Horizontal, Row 4) EGREETING (Horizontal, Row 8) SOCIAL NETWORK (Horizontal, Row 10) NEWSGROUP (Vertical, starting from ‘N’ in Row 1, Column 4, reading downwards to ‘P’ in Row 9, Column 4)
 Answers to textbook exercises
Answers to textbook exercises