Share
Explore

ThreatIQ Overview

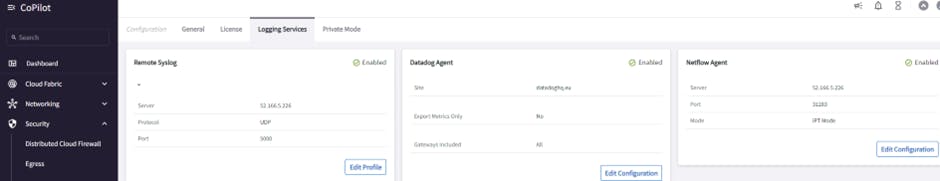
ABI Copilot ThreatIQ Alert
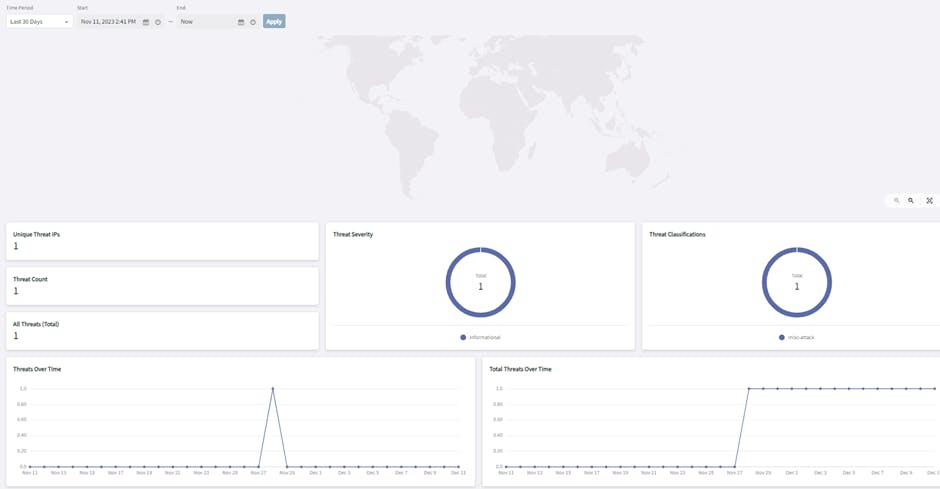

(Internet IP registrar) has details of which entity/organization the IP/IP block is registered with.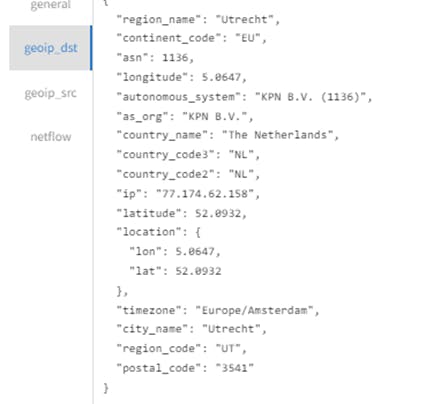
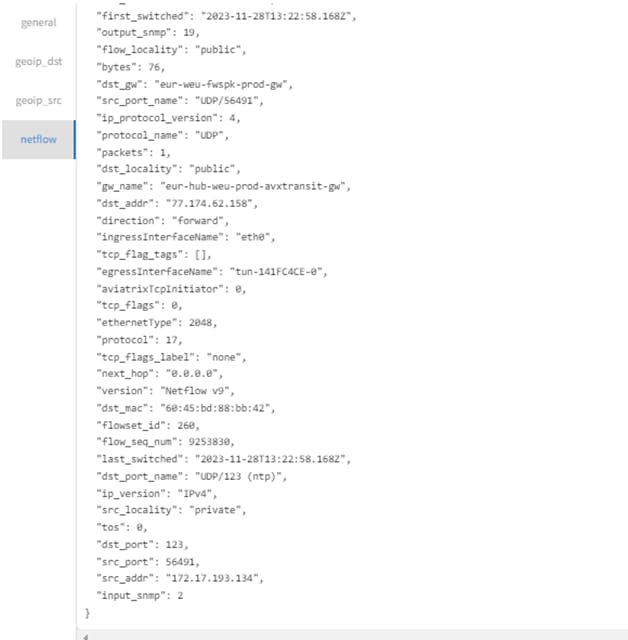
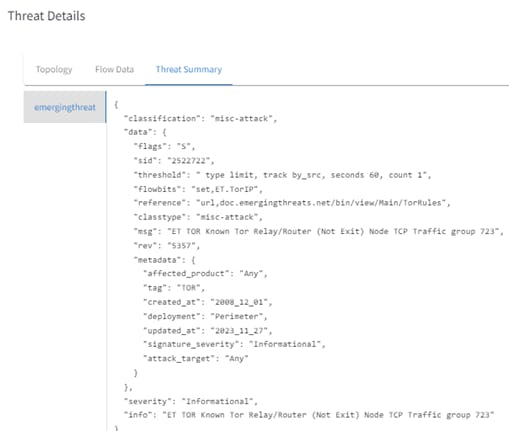
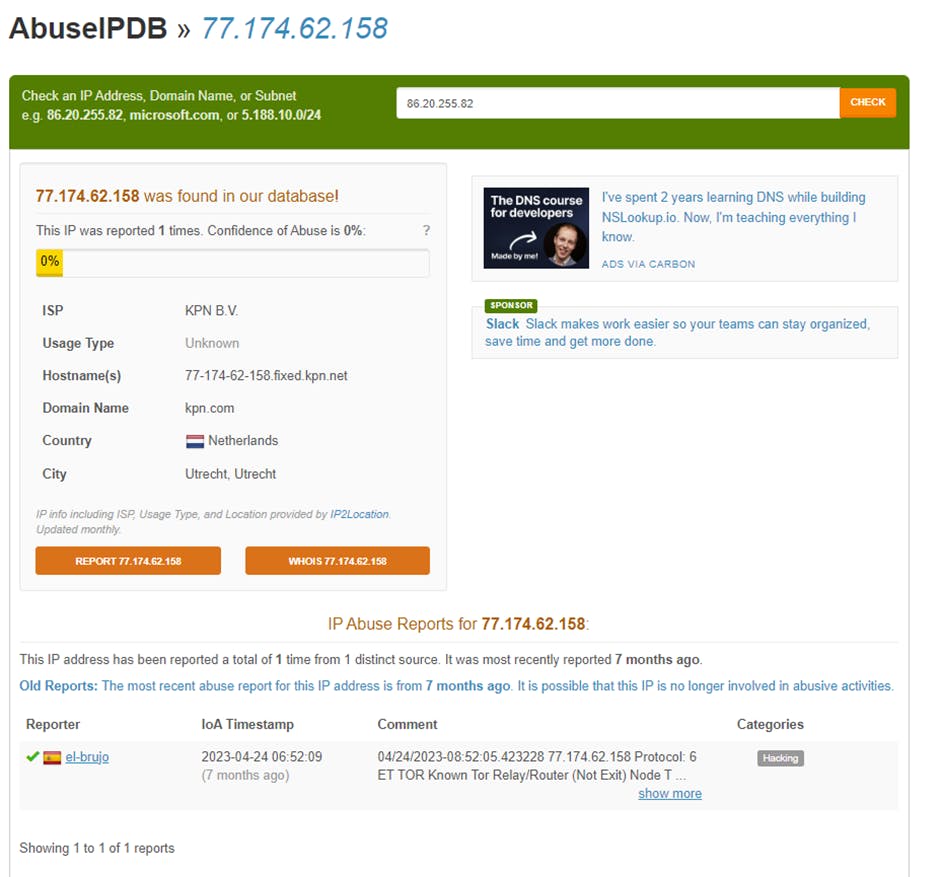

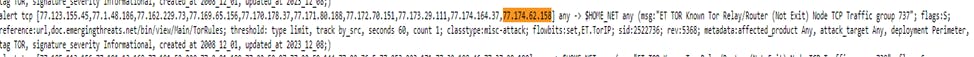
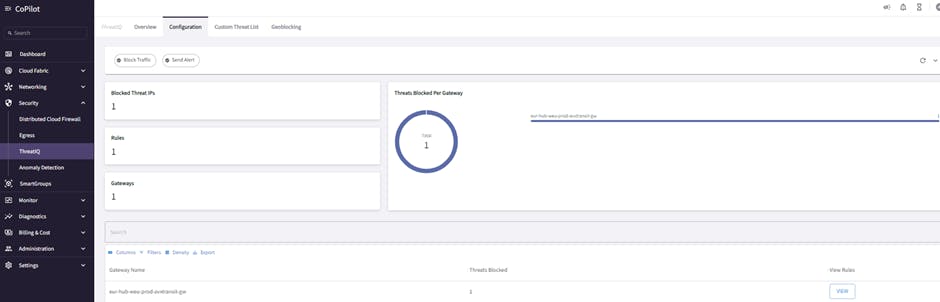
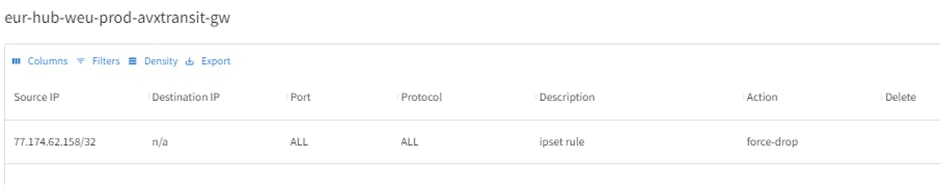
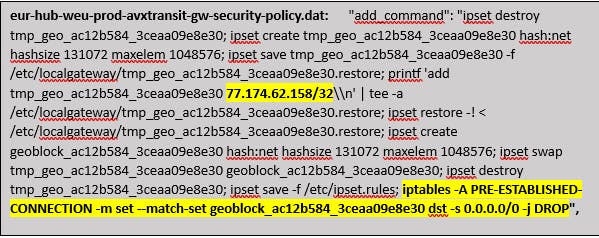
4.1 Example of Controller updating Aviatrix Gateway with IPSET rule
Want to print your doc?
This is not the way.
This is not the way.

Try clicking the ⋯ next to your doc name or using a keyboard shortcut (
CtrlP
) instead.