I Need Information Security
I Need Information Security
...written for my friends and family.
Disclaimer | Notice
This was written for friends and family, and not for Information Security (InfoSec) professionals.
Information security (InfoSec), Cybersecurity, Security...are used interchangeably...albeit not technically correct. Imagine this as a conversation between friends over a coffee/drinks. This is not professional/legal advice. Authors/editors have been in the InfoSec industry for a long time.
If you have suggestions, email:
Table of Contents
Basics
Information Security (InfoSec) vs Privacy vs Convenience

What do I want to protect?
Account / Password Protection
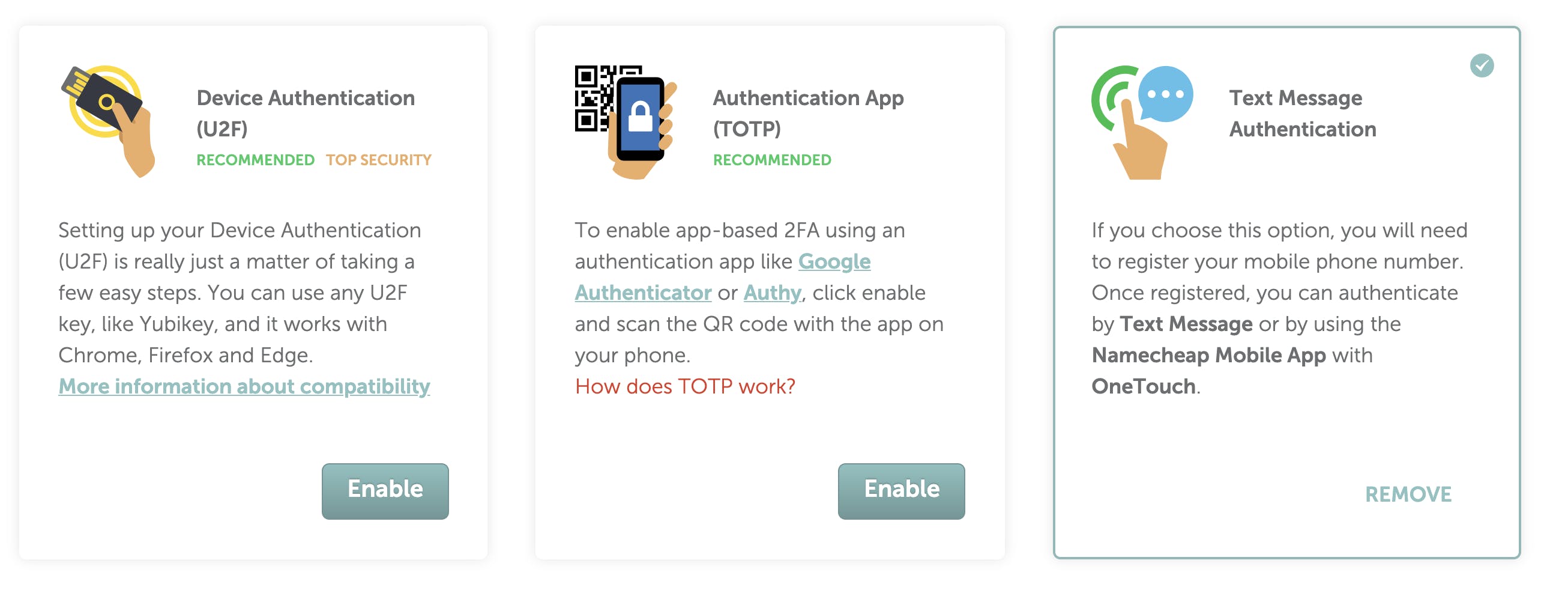
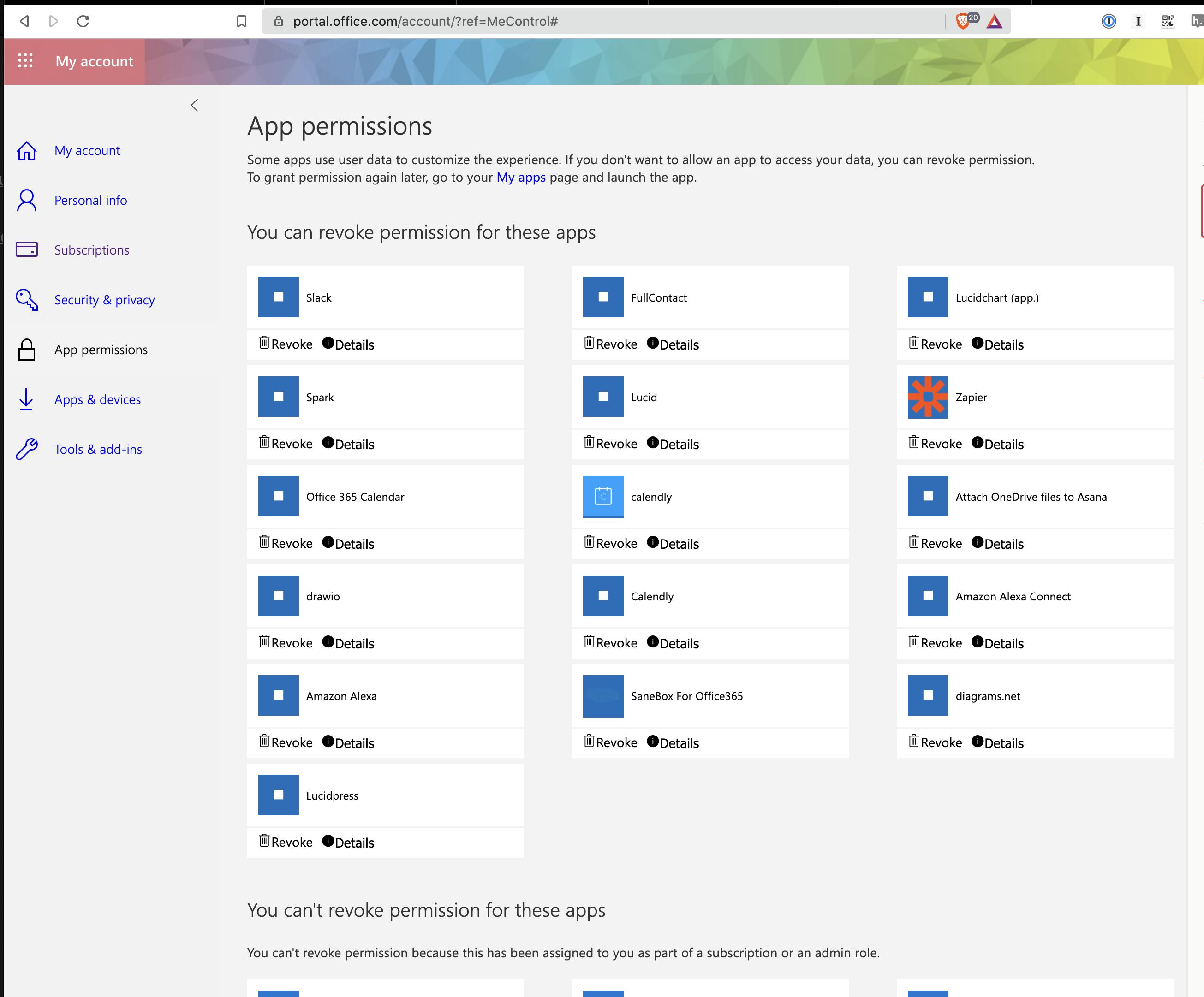
Anti-Virus Software
Phishing
Computer Backups
Home Network Security
Network Security
Content Filtering
Privacy (In Progress)
Want to print your doc?
This is not the way.
This is not the way.

Try clicking the ⋯ next to your doc name or using a keyboard shortcut (
CtrlP
) instead.